CompTIA SY0-601 Real Exam Questions
The questions for SY0-601 were last updated at Dec 10,2025.
- Exam Code: SY0-601
- Exam Name: CompTIA Security+ Exam
- Certification Provider: CompTIA
- Latest update: Dec 10,2025
Which of the following would MOST likely be identified by a credentialed scan but would be missed by an uncredentialed scan?
- A . Vulnerabilities with a CVSS score greater than 6.9.
- B . Critical infrastructure vulnerabilities on non-IP protocols.
- C . CVEs related to non-Microsoft systems such as printers and switches.
- D . Missing patches for third-party software on Windows workstations and servers.
A company was compromised, and a security analyst discovered the attacker was able to get access to a service account.
The following logs were discovered during the investigation:
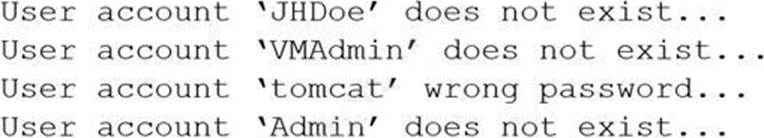
Which of the following MOST likely would have prevented the attacker from learning the service account name?
- A . Race condition testing
- B . Proper error handling
- C . Forward web server logs to a SIEM
- D . Input sanitization
one of the attendees starts to notice delays in the connection. and the HTTPS site requests are reverting to HTTP.
Which of the following BEST describes what is happening?
- A . Birthday collision on the certificate key
- B . DNS hacking to reroute traffic
- C . Brute force to the access point
- D . A SSL/TLS downgrade
The security team received a report of copyright infringement from the IP space of the corporate network. The report provided a precise time stamp for the incident as well as the name of the copyrighted files. The analyst has been tasked with determining the infringing source machine and instructed to implement measures to prevent such incidents from occurring again.
Which of the following is MOST capable of accomplishing both tasks?
- A . HIDS
- B . Allow list
- C . TPM
- D . NGFW
An organization wants seamless authentication to its applications.
Which of the following should the organization employ to meet this requirement?
- A . SOAP
- B . SAML
- C . SSO
- D . Kerberos
A business is looking for a cloud service provider that offers a la carte services, including cloud backups, VM elasticity, and secure networking.
Which of the following cloud service provider types should business engage?
- A . A laaS
- B . PaaS
- C . XaaS
- D . SaaS
A security administrator is setting up a SIEM to help monitor for notable events across the enterprise.
Which of the following control types does this BEST represent?
- A . Preventive
- B . Compensating
- C . Corrective
- D . Detective
A company is implementing a new SIEM to log and send alerts whenever malicious activity is blocked by its antivirus and web content filters.
Which of the following is the primary use case for this scenario?
- A . Implementation of preventive controls
- B . Implementation of detective controls
- C . Implementation of deterrent controls
- D . Implementation of corrective controls
Which of the following disaster recovery tests is the LEAST time consuming for the disaster recovery team?
- A . Tabletop
- B . Parallel
- C . Full interruption
- D . Simulation
During an incident, a company’s CIRT determines it is necessary to observe the continued network-based transactions between a callback domain and the malware running on an enterprise PC.
Which of the following techniques would be BEST to enable this activity while reducing the nsk of lateral spread and the risk that the adversary would notice any changes?
- A . Physically move the PC to a separate Internet point of presence.
- B . Create and apply microsegmentation rules,
- C . Emulate the malware in a heavily monitored DMZ segment
- D . Apply network blacklisting rules for the adversary domain
