CompTIA SY0-601 Real Exam Questions
The questions for SY0-601 were last updated at Dec 10,2025.
- Exam Code: SY0-601
- Exam Name: CompTIA Security+ Exam
- Certification Provider: CompTIA
- Latest update: Dec 10,2025
An analyst Is generating a security report for the management team. Security guidelines recommend disabling all listening unencrypted services.
Given this output from Nmap:
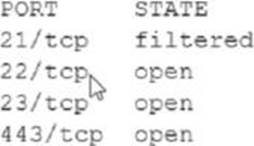
Which of the following should the analyst recommend to disable?
- A . 21/tcp
- B . 22/tcp
- C . 23/tcp
- D . 443/tcp
A security engineer needs to create a network segment that can be used for servers thal require connections from untrusted networks.
Which of the following should the engineer implement?
- A . An air gap
- B . A hot site
- C . A VUAN
- D . A screened subnet
A security researcher is tracking an adversary by noting its attacks and techniques based on its capabilities, infrastructure, and victims.
Which of the following is the researcher MOST likely using?
- A . The Diamond Model of Intrusion Analysis
- B . The Cyber Kill Chain
- C . The MITRE CVE database
- D . The incident response process
A desktop support technician recently installed a new document-scanning software program on a computer. However, when the end user tried to launch the program, it did not respond.
Which of the following is MOST likely the cause?
- A . A new firewall rule is needed to access the application.
- B . The system was quarantined for missing software updates.
- C . The software was not added to the application whitelist.
- D . The system was isolated from the network due to infected software
A network analyst is investigating compromised corporate information. The analyst leads to a theory that network traffic was intercepted before being transmitted to the internet.
The following output was captured on an internal host:

Based on the IoCS, which of the following was the MOST likely attack used to compromise the network communication?
- A . Denial of service
- B . ARP poisoning
- C . Command injection
- D . MAC flooding
After a WiFi scan of a local office was conducted, an unknown wireless signal was identified Upon investigation, an unknown Raspberry Pi device was found connected to an Ethernet port using a single connection.
Which of the following BEST describes the purpose of this device?
- A . loT sensor
- B . Evil twin
- C . Rogue access point
- D . On-path attack
Which of the following describes a maintenance metric that measures the average time required to troubleshoot and restore failed equipment?
- A . RTO
- B . MTBF
- C . MTTR
- D . RPO
Which of the following function as preventive, detective, and deterrent controls to reduce the risk of physical theft? (Select TWO).
- A . Mantraps
- B . Security guards
- C . Video surveillance
- D . Fences
- E . Bollards
- F . Antivirus
A global company is experiencing unauthorized logging due to credential theft and account lockouts caused by brute-force attacks. The company is considering implementing a third-party identity provider to help mitigate these attacks.
Which of the following would be the BEST control for the company to require from prospective vendors?
- A . IP restrictions
- B . Multifactor authentication
- C . A banned password list
- D . A complex password policy
Which of the following isa risk that is specifically associated with hesting applications iin the public cloud?
- A . Unsecured root accounts
- B . Zero day
- C . Shared tenancy
- D . Insider threat
