Microsoft SC-200 Real Exam Questions
The questions for SC-200 were last updated at Dec 11,2025.
- Exam Code: SC-200
- Exam Name: Microsoft Security Operations Analyst
- Certification Provider: Microsoft
- Latest update: Dec 11,2025
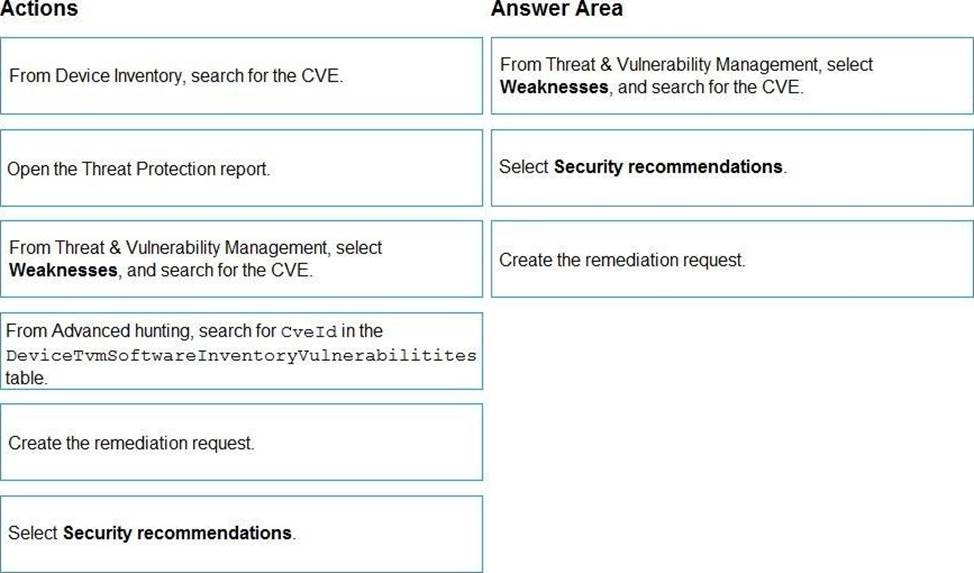
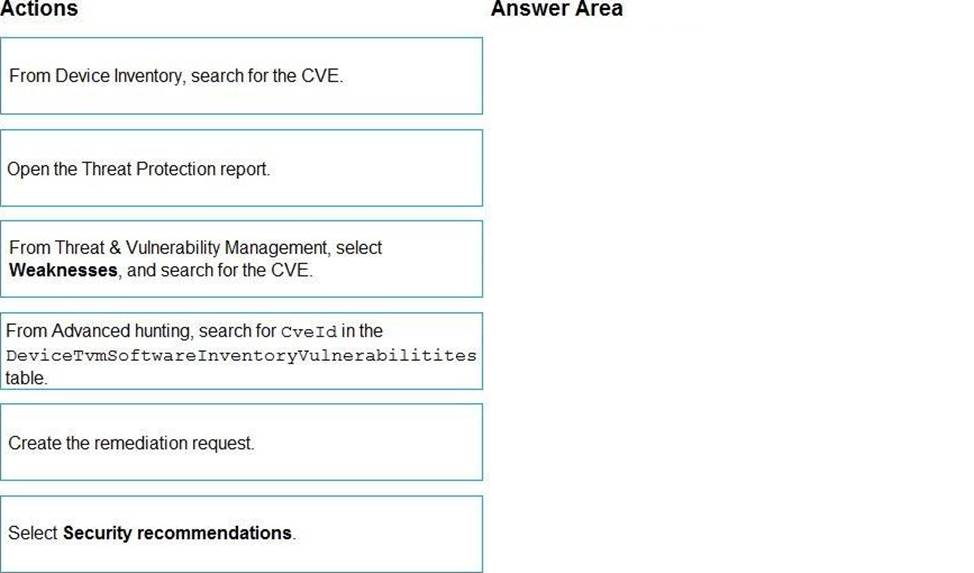
DRAG DROP
You are informed of a new common vulnerabilities and exposures (CVE) vulnerability that affects your environment.
You need to use Microsoft Defender Security Center to request remediation from the team responsible for the affected systems if there is a documented active exploit available.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You receive an alert from Azure Defender for Key Vault.
You discover that the alert is generated from multiple suspicious IP addresses.
You need to reduce the potential of Key Vault secrets being leaked while you investigate the issue. The solution must be implemented as soon as possible and must minimize the impact on legitimate users.
What should you do first?
- A . Modify the access control settings for the key vault.
- B . Enable the Key Vault firewall.
- C . Create an application security group.
- D . Modify the access policy for the key vault.
You provision a Linux virtual machine in a new Azure subscription.
You enable Azure Defender and onboard the virtual machine to Azure Defender.
You need to verify that an attack on the virtual machine triggers an alert in Azure Defender.
Which two Bash commands should you run on the virtual machine? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . cp /bin/echo ./asc_alerttest_662jfi039n
- B . ./alerttest testing eicar pipe
- C . cp /bin/echo ./alerttest
- D . ./asc_alerttest_662jfi039n testing eicar pipe
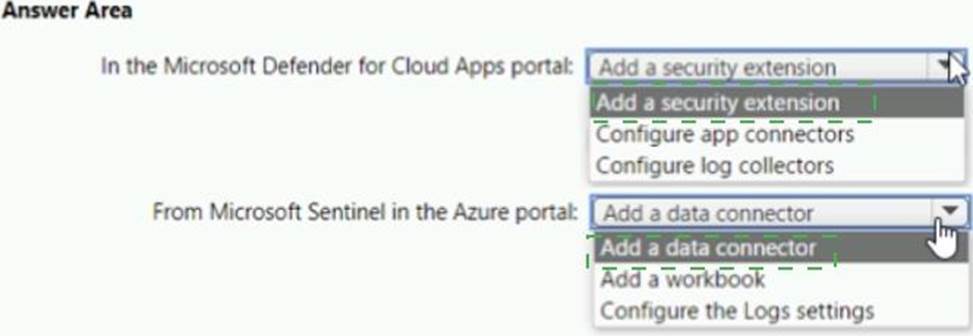
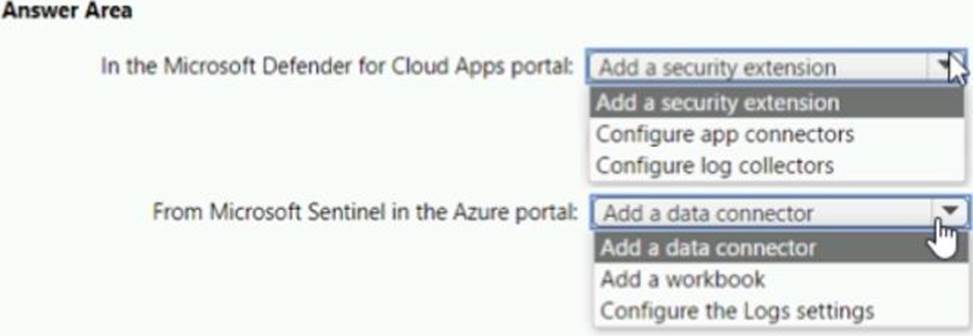
HOTSPOT
You need to configure the Microsoft Sentinel integration to meet the Microsoft Sentinel requirements.
What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring Microsoft Defender for Identity integration with Active Directory.
From the Microsoft Defender for identity portal, you need to configure several accounts for attackers to exploit.
Solution: From Entity tags, you add the accounts as Honeytoken accounts.
Does this meet the goal?
- A . Yes
- B . No
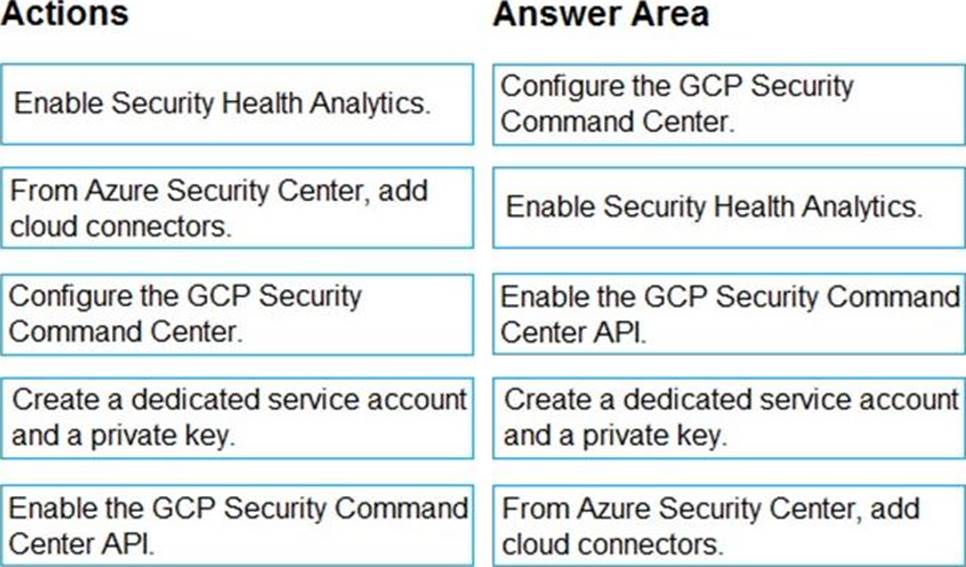
DRAG DROP
You have resources in Azure and Google cloud.
You need to ingest Google Cloud Platform (GCP) data into Azure Defender.
In which order should you perform the actions? To answer, move all actions from the list of actions to the answer area and arrange them in the correct order.

You need to complete the query for failed sign-ins to meet the technical requirements.
Where can you find the column name to complete the where clause?
- A . Security alerts in Azure Security Center
- B . Activity log in Azure
- C . Azure Advisor
- D . the query windows of the Log Analytics workspace