Microsoft SC-200 Real Exam Questions
The questions for SC-200 were last updated at Oct 13,2025.
- Exam Code: SC-200
- Exam Name: Microsoft Security Operations Analyst
- Certification Provider: Microsoft
- Latest update: Oct 13,2025
You receive a security bulletin about a potential attack that uses an image file.
You need to create an indicator of compromise (IoC) in Microsoft Defender for Endpoint to prevent the attack.
Which indicator type should you use?
- A . a URL/domain indicator that has Action set to Alert only
- B . a URL/domain indicator that has Action set to Alert and block
- C . a file hash indicator that has Action set to Alert and block
- D . a certificate indicator that has Action set to Alert and block
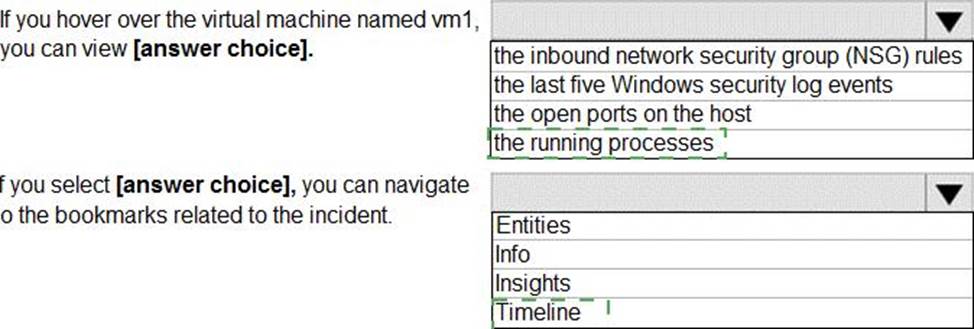
HOTSPOT
From Azure Sentinel, you open the Investigation pane for a high-severity incident as shown in the following exhibit.
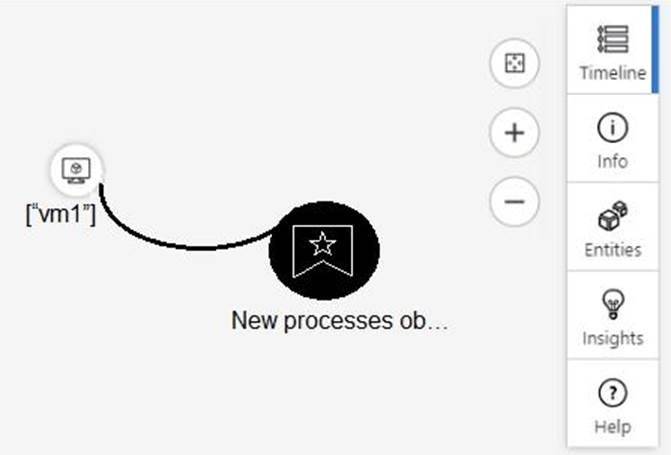
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
Your company uses line-of-business apps that contain Microsoft Office VBA macros.
You plan to enable protection against downloading and running additional payloads from the Office VBA macros as additional child processes.
You need to identify which Office VBA macros might be affected.
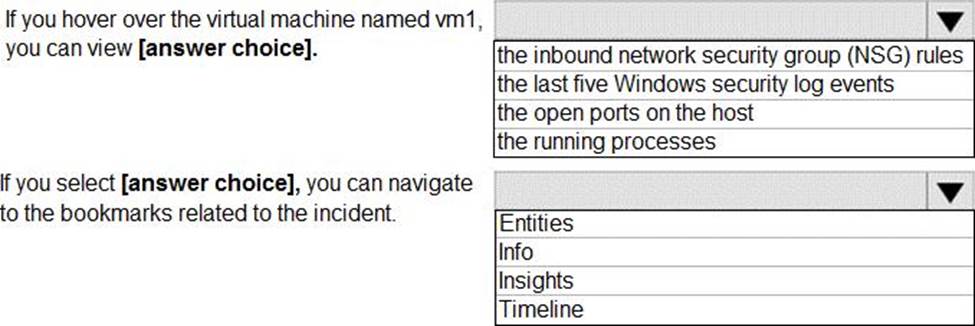
Which two commands can you run to achieve the goal? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
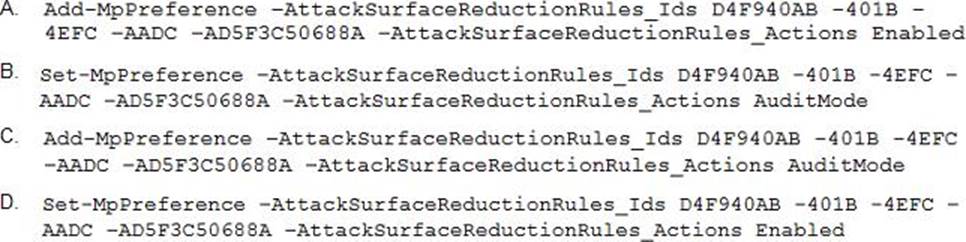
- A . Option A
- B . Option B
- C . Option C
- D . Option D
You need to visualize Azure Sentinel data and enrich the data by using third-party data sources to identify indicators of compromise (IoC).
What should you use?
- A . notebooks in Azure Sentinel
- B . Microsoft Cloud App Security
- C . Azure Monitor
- D . hunting queries in Azure Sentinel
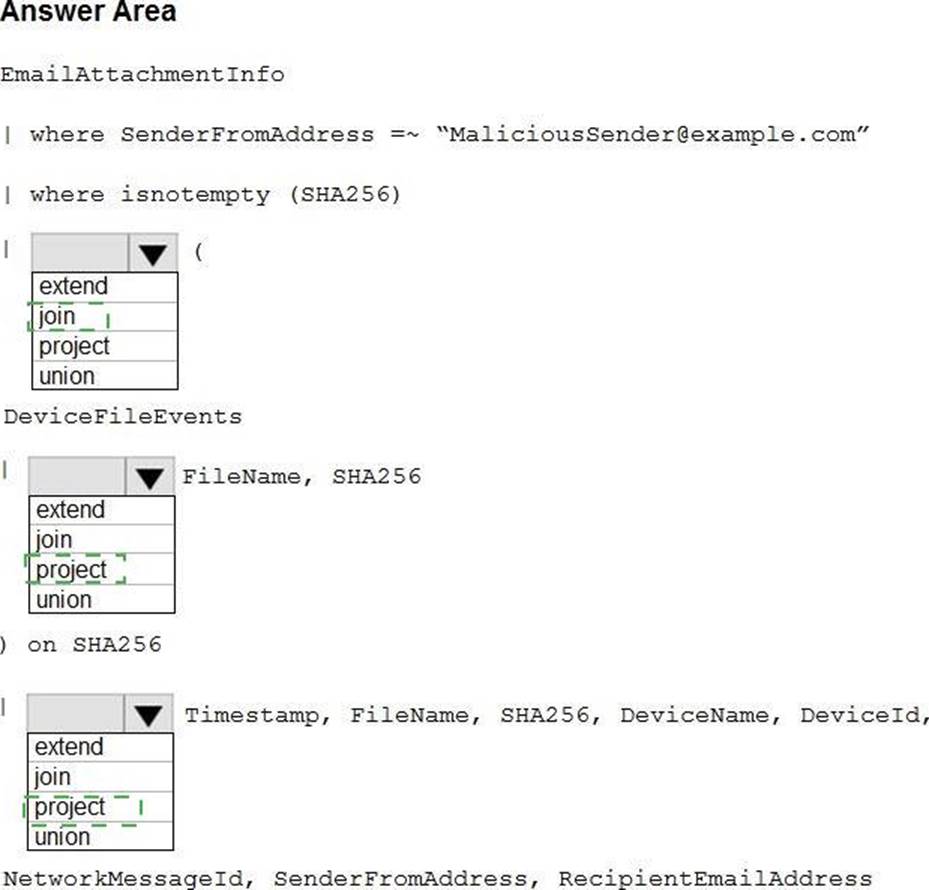
HOTSPOT
You have a Microsoft 365 E5 subscription.
You plan to perform cross-domain investigations by using Microsoft 365 Defender.
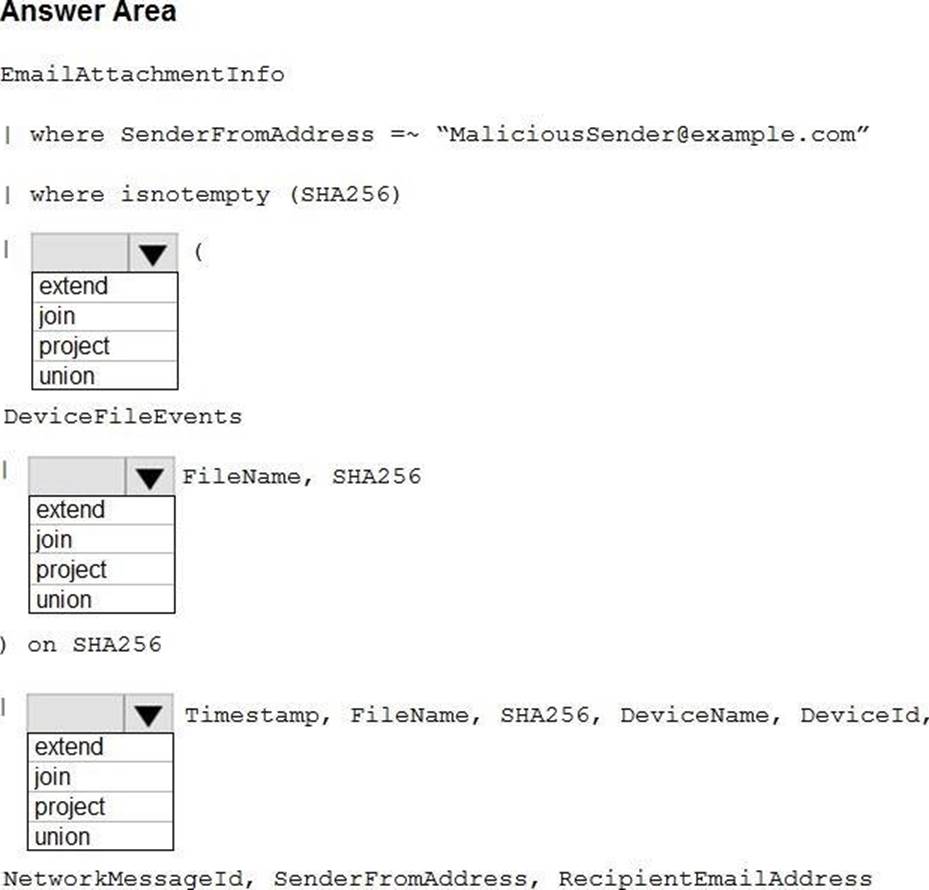
You need to create an advanced hunting query to identify devices affected by a malicious email attachment.
How should you complete the query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
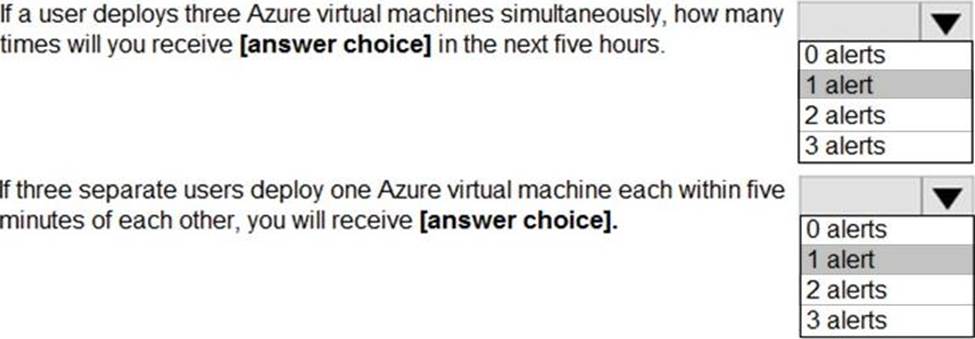
HOTSPOT
You use Azure Sentinel to monitor irregular Azure activity.
You create custom analytics rules to detect threats as shown in the following exhibit.
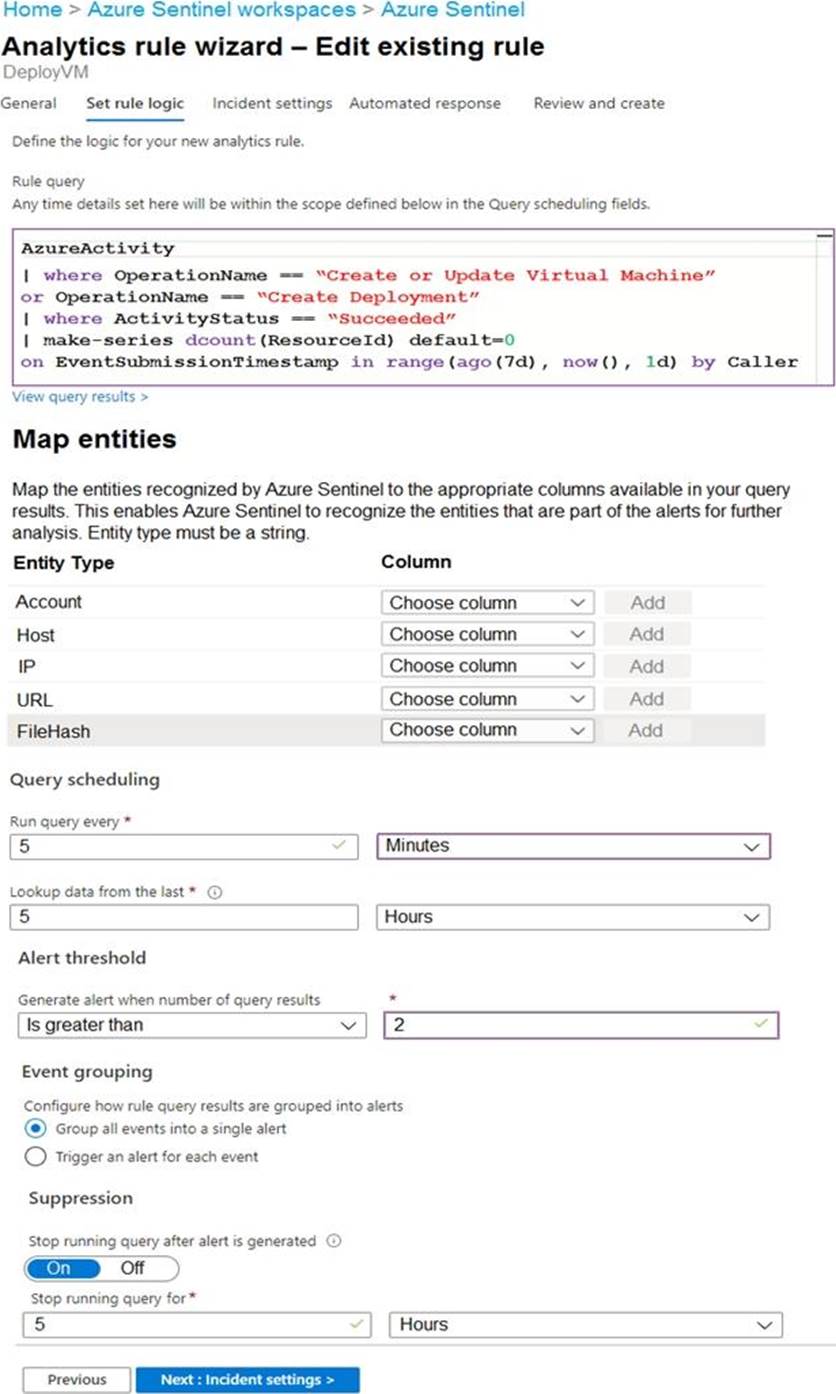
You do NOT define any incident settings as part of the rule definition.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
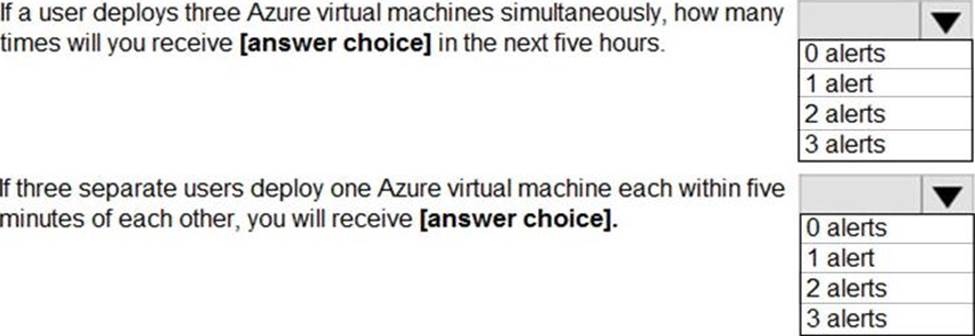
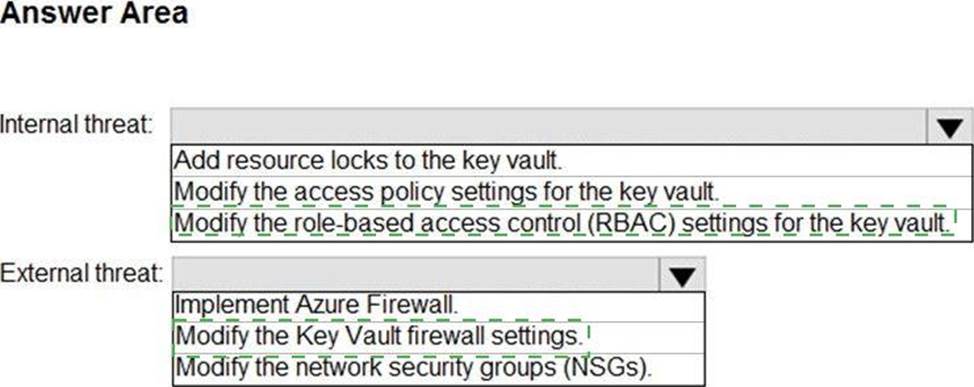
HOTSPOT for the Azure virtual
You need to recommend remediation actions for the Azure Defender alerts for Fabrikam.
What should you recommend for each threat? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
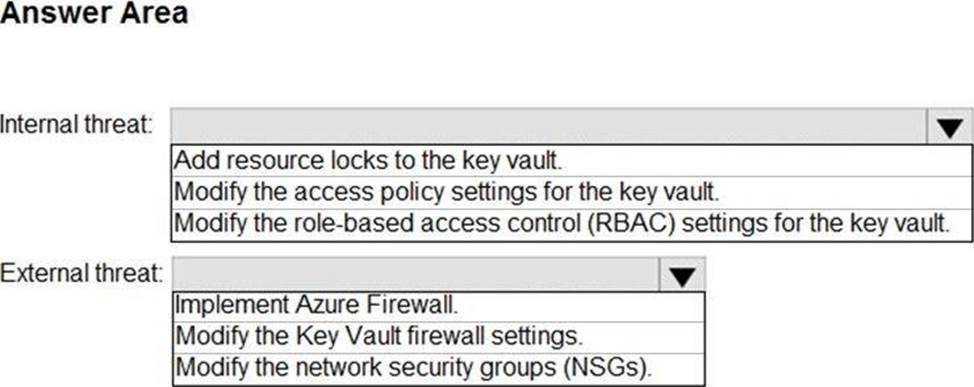
You need to create the test rule to meet the Azure Sentinel requirements.
What should you do when you create the rule?
- A . From Set rule logic, turn off suppression.
- B . From Analytics rule details, configure the tactics.
- C . From Set rule logic, map the entities.
- D . From Analytics rule details, configure the severity.
You create an Azure subscription named sub1.
In sub1, you create a Log Analytics workspace named workspace1.
You enable Azure Security Center and configure Security Center to use workspace1.
You need to ensure that Security Center processes events from the Azure virtual machines that report to workspace1.
What should you do?
- A . In workspace1, install a solution.
- B . In sub1, register a provider.
- C . From Security Center, create a Workflow automation.
- D . In workspace1, create a workbook.
You implement Safe Attachments policies in Microsoft Defender for Office 365.
Users report that email messages containing attachments take longer than expected to be received.
You need to reduce the amount of time it takes to deliver messages that contain attachments without compromising security. The attachments must be scanned for malware, and any messages that contain malware must be blocked.
What should you configure in the Safe Attachments policies?
- A . Dynamic Delivery
- B . Replace
- C . Block and Enable redirect
- D . Monitor and Enable redirect