CompTIA PT0-002 Real Exam Questions
The questions for PT0-002 were last updated at Apr 15,2025.
- Exam Code: PT0-002
- Exam Name: CompTIA PenTest+ Certification Exam
- Certification Provider: CompTIA
- Latest update: Apr 15,2025
A company uses a cloud provider with shared network bandwidth to host a web application on dedicated servers. The company’s contact with the cloud provider prevents any activities that would interfere with the cloud provider’s other customers.
When engaging with a penetration-testing company to test the application, which of the following should the company avoid?
- A . Crawling the web application’s URLs looking for vulnerabilities
- B . Fingerprinting all the IP addresses of the application’s servers
- C . Brute forcing the application’s passwords
- D . Sending many web requests per second to test DDoS protection
During an assessment, a penetration tester manages to exploit an LFI vulnerability and browse the web log for a target Apache server.
Which of the following steps would the penetration tester most likely try NEXT to further exploit the web server? (Choose two.)
- A . Cross-site scripting
- B . Server-side request forgery
- C . SQL injection
- D . Log poisoning
- E . Cross-site request forgery
- F . Command injection
A penetration tester was brute forcing an internal web server and ran a command that produced the following output:
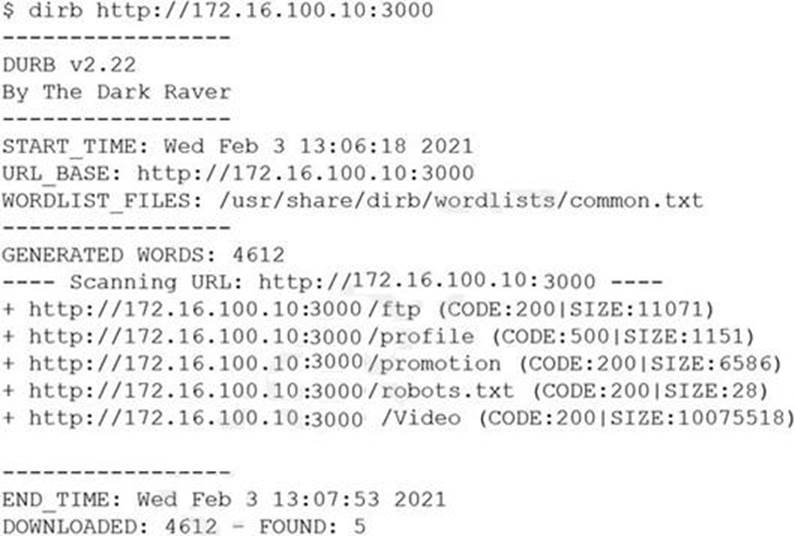
However, when the penetration tester tried to browse the URL http://172.16.100.10:3000/profile, a blank page was displayed.
Which of the following is the MOST likely reason for the lack of output?
- A . The HTTP port is not open on the firewall.
- B . The tester did not run sudo before the command.
- C . The web server is using HTTPS instead of HTTP.
- D . This URI returned a server error.
Performing a penetration test against an environment with SCADA devices brings additional safety risk because the:
- A . devices produce more heat and consume more power.
- B . devices are obsolete and are no longer available for replacement.
- C . protocols are more difficult to understand.
- D . devices may cause physical world effects.
A penetration tester is reviewing the following SOW prior to engaging with a client:
“Network diagrams, logical and physical asset inventory, and employees’ names are to be treated as client confidential. Upon completion of the engagement, the penetration tester will submit findings to the client’s Chief Information Security Officer (CISO) via encrypted protocols and subsequently dispose of all findings by erasing them in a secure manner.”
Based on the information in the SOW, which of the following behaviors would be considered unethical? (Choose two.)
- A . Utilizing proprietary penetration-testing tools that are not available to the public or to the client for auditing and inspection
- B . Utilizing public-key cryptography to ensure findings are delivered to the CISO upon
completion of the
engagement - C . Failing to share with the client critical vulnerabilities that exist within the client architecture to appease the client’s senior leadership team
- D . Seeking help with the engagement in underground hacker forums by sharing the client’s public IP address
- E . Using a software-based erase tool to wipe the client’s findings from the penetration tester’s laptop
- F . Retaining the SOW within the penetration tester’s company for future use so the sales team can plan future engagements
A client evaluating a penetration testing company requests examples of its work.
Which of the following represents the BEST course of action for the penetration testers?
- A . Redact identifying information and provide a previous customer’s documentation.
- B . Allow the client to only view the information while in secure spaces.
- C . Determine which reports are no longer under a period of confidentiality.
- D . Provide raw output from penetration testing tools.
A penetration tester writes the following script:
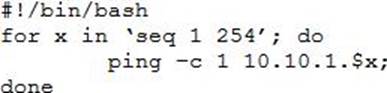
Which of the following objectives is the tester attempting to achieve?
- A . Determine active hosts on the network.
- B . Set the TTL of ping packets for stealth.
- C . Fill the ARP table of the networked devices.
- D . Scan the system on the most used ports.
A penetration tester successfully performed an exploit on a host and was able to hop from VLAN 100 to VLAN 200. VLAN 200 contains servers that perform financial transactions, and the penetration tester now wants the local interface of the attacker machine to have a static ARP entry in the local cache.
The attacker machine has the following:
IP Address: 192.168.1.63
Physical Address: 60-36-dd-a6-c5-33
Which of the following commands would the penetration tester MOST likely use in order to establish a static ARP entry successfully?
- A . tcpdump -i eth01 arp and arp[6:2] == 2
- B . arp -s 192.168.1.63 60-36-DD-A6-C5-33
- C . ipconfig /all findstr /v 00-00-00 | findstr Physical
- D . route add 192.168.1.63 mask 255.255.255.255.0 192.168.1.1
A penetration tester recently performed a social-engineering attack in which the tester found an employee of the target company at a local coffee shop and over time built a relationship with the employee. On the employee’s birthday, the tester gave the employee an external hard drive as a gift.
Which of the following social-engineering attacks was the tester utilizing?
- A . Phishing
- B . Tailgating
- C . Baiting
- D . Shoulder surfing
Which of the following commands will allow a penetration tester to permit a shell script to be executed by the file owner?
- A . chmod u+x script.sh
- B . chmod u+e script.sh
- C . chmod o+e script.sh
- D . chmod o+x script.sh
