Paloalto Networks PCCET Real Exam Questions
The questions for PCCET were last updated at Jul 08,2025.
- Exam Code: PCCET
- Exam Name: Palo Alto Networks Certified Cybersecurity Entry-level Technician
- Certification Provider: Paloalto Networks
- Latest update: Jul 08,2025
Why is it important to protect East-West traffic within a private cloud?
- A . All traffic contains threats, so enterprises must protect against threats across the entire network
- B . East-West traffic contains more session-oriented traffic than other traffic
- C . East-West traffic contains more threats than other traffic
- D . East-West traffic uses IPv6 which is less secure than IPv4
Which Palo Alto Networks tool is used to prevent endpoint systems from running malware executables such as viruses, trojans, and rootkits?
- A . Expedition
- B . Cortex XDR
- C . AutoFocus
- D . App-ID
Which product from Palo Alto Networks extends the Security Operating Platform with the global threat intelligence and attack context needed to accelerate analysis, forensics, and hunting workflows?
- A . Global Protect
- B . WildFire
- C . AutoFocus
- D . STIX
Why have software developers widely embraced the use of containers?
- A . Containers require separate development and production environments to promote authentic code.
- B . Containers share application dependencies with other containers and with their host computer.
- C . Containers simplify the building and deploying of cloud native applications.
- D . Containers are host specific and are not portable across different virtual machine hosts.
On an endpoint, which method is used to protect proprietary data stored on a laptop that has been stolen?
- A . operating system patches
- B . full-disk encryption
- C . periodic data backups
- D . endpoint-based firewall
In the attached network diagram, which device is the switch?
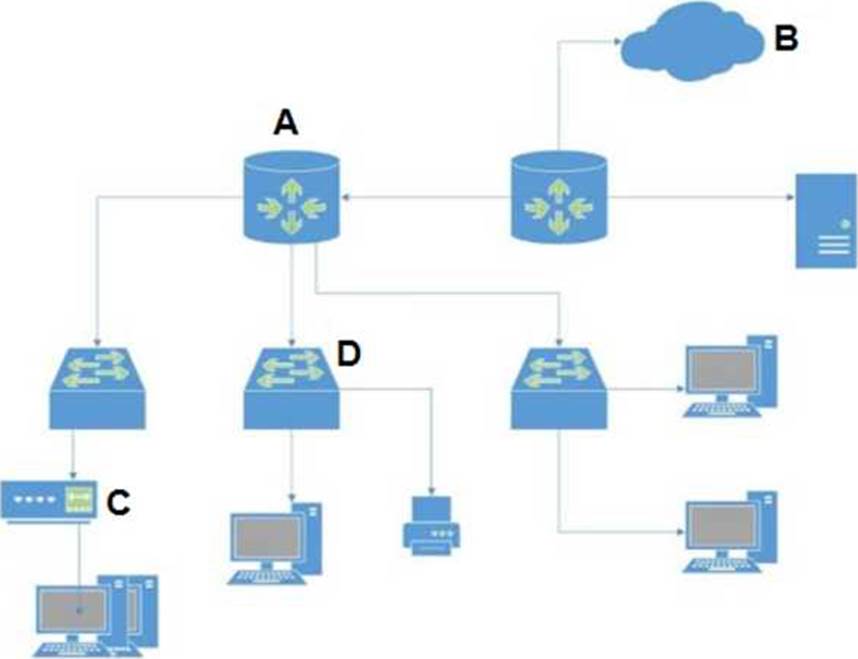
- A . A
- B . B
- C . C
- D . D
What is the primary security focus after consolidating data center hypervisor hosts within trust levels?
- A . control and protect inter-host traffic using routers configured to use the Border Gateway Protocol (BGP) dynamic routing protocol
- B . control and protect inter-host traffic by exporting all your traffic logs to a sysvol log server using the User Datagram Protocol (UDP)
- C . control and protect inter-host traffic by using IPv4 addressing
- D . control and protect inter-host traffic using physical network security appliances
Which option would be an example of PII that you need to prevent from leaving your enterprise network?
- A . Credit card number
- B . Trade secret
- C . National security information
- D . A symmetric encryption key
What are two key characteristics of a Type 1 hypervisor? (Choose two.)
- A . is hardened against cyber attacks
- B . runs without any vulnerability issues
- C . runs within an operating system
- D . allows multiple, virtual (or guest) operating systems to run concurrently on a single physical host computer
