Huawei H12-725_V4.0-ENU Real Exam Questions
The questions for H12-725_V4.0-ENU were last updated at Dec 16,2025.
- Exam Code: H12-725_V4.0-ENU
- Exam Name: HCIP-Security V4.0
- Certification Provider: Huawei
- Latest update: Dec 16,2025
Question #31
As shown in the figure, the primary and secondary backup networking based on VRRP is wrong. In the following description of this scenario, which one is wrong?
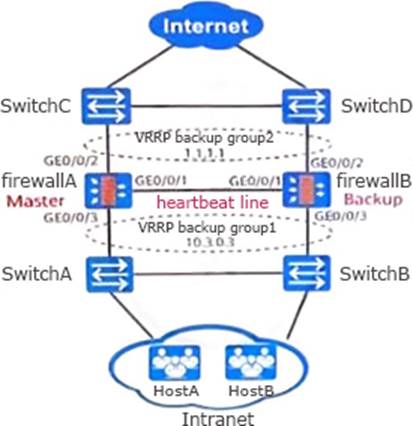
- A . In order to ensure the consistency of link switching, the firewall implements device status management based on VGMP groups.
- B . The configuration and status information of firewall A is backed up to firewall B in real time through the GE0/0/3 interface.
- C . Dual-machine hot backup can improve network reliability
- D . The firewall GE0/0/1 interface is the heartbeat interface, and the connected line is the heartbeat line.
Question #32
Which of the following descriptions about HTTP Flood defense is incorrect?
- A . If the free proxy used during the attack supports the redirection function, the basic mode defense will be ineffective.
- B . The source authentication defense method is to defend against HTTP
- C . Defense based on enhanced mode can determine whether the TTP access is initiated by a real user by asking the user to enter a verification code.
- D . Defense based on basic mode cannot effectively prevent access from non-browser clients
Question #33
Which of the following descriptions about dual-machine hot standby is incorrect?
- A . In a load-sharing network, the configuration command can be backed up from "Configure Standby Device" to "Configure Primary Device"
- B . In an active-standby backup network, configuration commands and status information are backed up from the active device to the standby device.
- C . In load-sharing mode networking, traffic is processed by two devices, which can bear greater peak traffic than active-standby backup mode or mirroring mode networking.
- D . In a load-sharing network, both firewalls are active devices. Therefore, if the two active devices are allowed to back up each other’s commands, it may cause the problems of mutual overwriting or conflict between the commands of the two devices.
Question #34
Which of the following descriptions of cleaning centers is incorrect?
- A . Back-injection methods include: policy routing back-injection, static route back-injection, VPN back-injection and Layer 2 back-injection.
- B . The cleaning device supports rich and flexible attack prevention technologies, but cannot defend against CC attacks and ICMP Flood attacks.
- C . There are two methods of traffic diversion: static traffic diversion and dynamic traffic diversion.
- D . The cleaning center completes functions such as diversion and cleaning of abnormal traffic, and reinjection of cleaned traffic.
