Huawei H12-725_V4.0-ENU Real Exam Questions
The questions for H12-725_V4.0-ENU were last updated at Dec 22,2025.
- Exam Code: H12-725_V4.0-ENU
- Exam Name: HCIP-Security V4.0
- Certification Provider: Huawei
- Latest update: Dec 22,2025
In which of the following access authentication methods, the terminal must obtain an IP address before authentication?
- A . 802.1×Authentication
- B . Portal
- C . MAC authentication
- D . MAC bypass authentication
Which of the following is not an implementation process of bandwidth management?
- A . Bandwidth channel
- B . Traffic Analysis
- C . Interface speed limit
- D . Bandwidth policy
As shown in the figure, the firewall is deployed as a gateway dual-machine hot standby, and the upstream and downstream devices are switches.
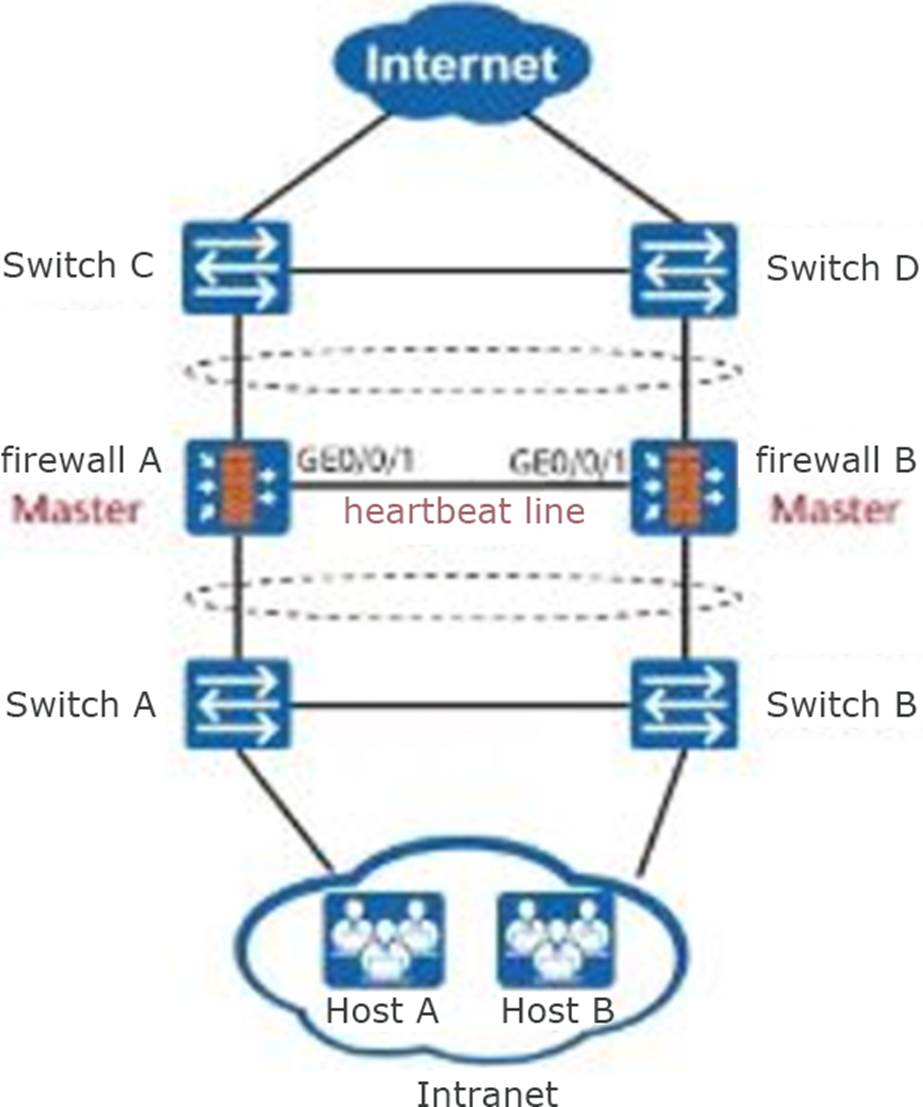
To achieve round-trip traffic load balancing, at least how many VRRP backup groups need to be configured in this scenario?
- A . 4
- B . 6
- C . 2
- D . 3
How many levels of bandwidth policies does the firewall support?
- A . 2
- B . 5
- C . 4
- D . 3
Which of the following descriptions about the characteristics of Eth-Trunk is incorrect?
- A . Eth-Trunk can be a Layer 2 interface or a Layer 3 interface.
- B . Eth-Trunk is a logical interface
- C . There are at least 2 Eth-Trunk member links
- D . There is at least 1 active Eth-Trunk link
Which of the following descriptions about the characteristics of Eth-Trunk is incorrect?
- A . Eth-Trunk can be a Layer 2 interface or a Layer 3 interface.
- B . Eth-Trunk is a logical interface
- C . There are at least 2 Eth-Trunk member links
- D . There is at least 1 active Eth-Trunk link
Which of the following descriptions of virtual interfaces is incorrect?
- A . Mutual access between virtual systems is achieved through virtual interfaces
- B . The link layer and protocol layer of the virtual interface are always UP
- C . The virtual interface of the root system is Virtual-if1
- D . The format of the virtual interface is "Virtual-if+interface number"
Which authentication method is generally used in situations where new networks are built, users are concentrated, and information security requirements are strict?
- A . Portal certification
- B . 802.1x authentication
- C . MAC priority Porta1 authentication
- D . MAC authentication
Which of the following is not a function of the Anti-DDoS Management Center?
- A . Performance management
- B . Strategic Management
- C . Alarm management
- D . Traffic detection
The administrator has defined two keywords that need to be identified on the firewall. The keyword administrator has defined two keywords that need to be identified on the firewall. The weight value of keyword X is 2 and the weight value of keyword Y is 3. The alarm threshold for content filtering is defined as 5 and the blocking threshold is 10. If the device detects that the keyword X exists once and the keyword Y twice exists in the webpage browsed by the user.
Regarding the weight value and the behavior of users accessing web pages, which of the following statements is correct?
- A . The weight value is 8 and you can access the web page
- B . The weight value is 10 and the web page cannot be accessed.
- C . The weight value is 8 and the web page cannot be accessed.
- D . The weight value is 10 and you can access the web page
