DELL EMC D-PSC-DS-23 Real Exam Questions
The questions for D-PSC-DS-23 were last updated at Jan 23,2026.
- Exam Code: D-PSC-DS-23
- Exam Name: Dell PowerScale Design 2023 Exam
- Certification Provider: DELL EMC
- Latest update: Jan 23,2026
Which Isilon tool can be run from the cluster to display Isilon statistics such as CPU activity?
- A . iperf
- B . iostat
- C . InsightIQ
- D . MiTrend
Refer to Exhibit below.
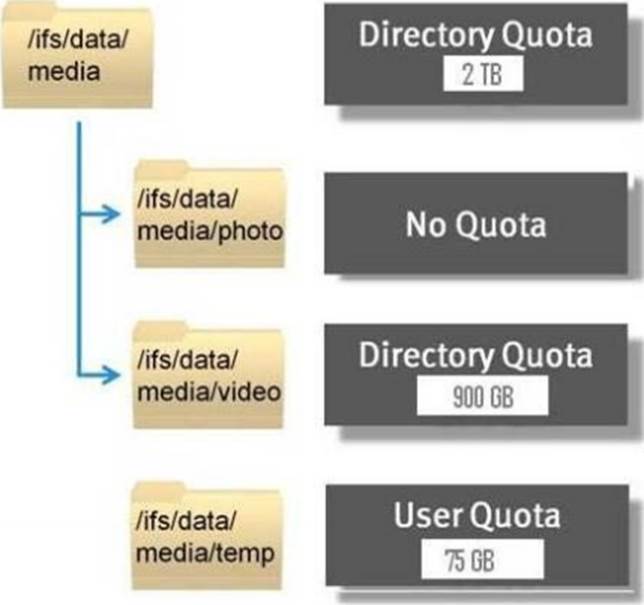
What is represented by the information shown in the exhibit?
- A . Directory quota cannot exceed 2 TB for both /ifs/data/media and /ifs/data/media/photo.
Directory quota cannot exceed 900 GB for /ifs/data/media/video.
Directory quota can be any size up to 2 TB and each user can only store 75 GB for /ifs/data/media/temp. - B . Directory quota cannot exceed 2 TB for /ifs/data/media and no quota limit on /ifs/data/media/photo.
Directory quota cannot exceed 900 GB for /ifs/data/media/video.
Directory quota can be any size up to 2 TB and each user can only store 75 GB for /ifs/data/media/temp. - C . Directory quota cannot exceed 2 TB for both /ifs/data/media and /ifs/data/media/photo.
Directory quota cannot exceed 900 GB for /ifs/data/media/video.
Directory quota can be any size up to 2 TB for /ifs/data/media/temp. - D . Directory quota cannot exceed 2 TB for both /ifs/data/media and /ifs/data/media/photo.
Directory quota cannot exceed 900 GB for /ifs/data/media/video.
Directory quota can be any size up to 900 GB and each user can only store 75 GB for /ifs/data/media/temp.
Which tool is used to perform a cluster-wide kernel configuration change on an Isilon Gen 6 cluster?
- A . gconfig
- B . isi_tardis
- C . isi_for_array
- D . sysct1
You are designing a backup solution using an NDMP redirector and throttler.
What is the default threshold percentage of CPU resources that the throttler limits NDMP to?
- A . 25
- B . 45
- C . 50
- D . 60
A customer is evaluating PowerScale and NetApp FAS solutions. They are storing many unique files and want to understand how each solution deduplicates data.
What is the difference between how PowerScale and NetApp FAS deduplicate data?
- A . PowerScale uses separate deduplication at the volume level.
NetApp FAS uses global deduplication across the cluster. - B . PowerScale uses global deduplication across the cluster.
NetApp FAS separates deduplication at the volume level. - C . PowerScale does not have deduplication.
NetApp FAS uses local deduplication. - D . PowerScale uses local deduplication.
NetApp FAS does not have deduplication.
Following Dell best practices, at what capacity consumption should an organization begin the process of ordering more nodes to add to a cluster?
- A . 80%
- B . 85%
- C . 75%
- D . 70%
A large manufacturing company is an existing Isilon customer with a cluster consisting of four NL400 nodes with 4TB drives. The cluster is using N+2:1 protection level and the file system shows that it is 60% utilized. Home directories and file shares comprise 75% of the existing content and the remainder is inactive deep archive. The company has 1,000 employees using Windows and Mac clients participating in a single Active Directory (AD) forest.
During a meeting with the CIO and Director of IT you discuss the company’s recent acquisition – an engineering firm that specializes in Computer Aided Design (CAD). The engineering firm has 400 UNIX workstations that produce technical drawings which are currently stored on another vendor’s SAN solution. The all UNIX environment uses NIS for authentication and name resolution. They do not currently use DNS or LDAP. The engineering company has an old storage system that has been experiencing problems and the CIO would like you to migrate the data onto the Isilon cluster. The CIO would like to eliminate all tape and recover the data onto disk.
The CIO is concerned about security of the company’s intellectual property, especially with the rapid adoption of mobile devices and external cloud content sharing services such as DropBox, Egnyte, and SugarSync. They would like to implement an alternative that provides external file sharing and mobile device synchronization while maintaining security control over the company’s data.
The Director of IT reports that users are storing non-work related content on the Isilon cluster. They would like to limit the amount of capacity that each user can consume in their home directory and want to ensure you provide the capability to easily visualize which users are over their allotment. The company’s Windows users currently leverage Windows Shadow Copy to recover files that have been accidentally deleted. The IT department wants to ensure that Mac and incoming UNIX clients have the same functionality.
The Director of IT also mentions that users are reporting slow response times when browsing their home directories and shared folders. They are concerned that Isilon cannot scale to support their combined requirements.
The customer provides the following environment summary from the engineering firm’s recently departed IT staff:
– 20 TB of Home Directory data
– 100 TB of active CAD projects
– 400 TB of archived data stored on tape at an offsite warehouse
The CIO approaches you with a new requirement. They would like to reuse the tape library that was previously used for archiving to now be used to back up some of their data.
What do you recommend to the Director of IT as the best architecture to achieve this goal?
- A . Connect the Tape Library via Fibre Channel to the Isilon cluster and use a third party backup software to initiate an NDMP backup to an accelerator.
- B . Implement a Backup Accelerator and use the internal backup software within the Isilon cluster to move data to the tape library.
- C . Use a Backup Accelerator with SynclQ to push the data to the tape library via the Fibre Channel ports on the accelerator.
- D . Use a third party backup software and have the Isilon cluster convert the data to LTFS so it can be stored to the tape library.
A customer has a 5 node Isilon cluster. The raw capacity of the cluster is 85% used. On average, the cluster has 4,000 users connected during office hours. The average CPU usage is 65%. The customer needs to delete some data to free up capacity.
What should the customer do to minimize the effect of the deletion job?
- A . Delete the data from a client directly connected to the cluster
- B . Run the treedelete job with a high impact and high priority during out-of-office hours.
- C . Run the treedelete job with a high impact and high priority during office hours.
- D . Run the treedelete job with the default impact and priority during out-of-office hours.
What method does the MediaScan job leverage to locate and clear media-level errors?
- A . MD5
- B . FEC
- C . SHA256
- D . CRC
What are characteristics of the streaming data access pattern on a PowerScale Gen6 cluster?
- A . Single stream workflows, very aggressive prefetching
- B . Clients accessing the same data, aggressive prefetching
- C . Multiple stream workflows, no prefetching
- D . Clients accessing the same data, moderate prefetching
