DELL EMC D-CSF-SC-23 Real Exam Questions
The questions for D-CSF-SC-23 were last updated at Apr 12,2025.
- Exam Code: D-CSF-SC-23
- Exam Name: NIST Cybersecurity Framework 2023 Exam
- Certification Provider: DELL EMC
- Latest update: Apr 12,2025
What specifically addresses cyber-attacks against an organization’s IT systems?
- A . Continuity of Support Plan
- B . Business Continuity Plan
- C . Continuity of Operations Plan
- D . Incident Response Plan
At what cyber kill chain stage do attackers use malware to exploit specific software or hardware vulnerabilities on the target, based on the information retrieved at the reconnaissance stage?
- A . Installation
- B . Reconnaissance
- C . Weaponization
- D . Delivery
What is used to ensure an organization understands the security risk to operations, assets, and individuals?
- A . Risk Management Strategy
- B . Risk Assessment
- C . Operational Assessment
- D . Risk Profile
To generate an accurate risk assessment, organizations need to gather information in what areas?
- A . Assets, Threats, Vulnerabilities, and Impact
- B . Assets, Vulnerabilities, Security, and Response
- C . Inventory, Security, Response, and Impact
- D . Inventory, Threats, Security, and Impact
The CSF recommends that the Communication Plan for an IRP include audience, method of communication, frequency, and what other element?
- A . Incident category
- B . Message criteria
- C . Incident severity
- D . Templates to use
A company failed to detect a breach of their production system. The breach originated from a legacy system that was originally thought to be decommissioned. It turned out that system was still operating and occasionally connected to the production system for reporting purposes.
Which part of the process failed?
- A . DE.CM
- B . ID.BE
- C . ID.AM
- D . PR.DS
Refer to the exhibit.
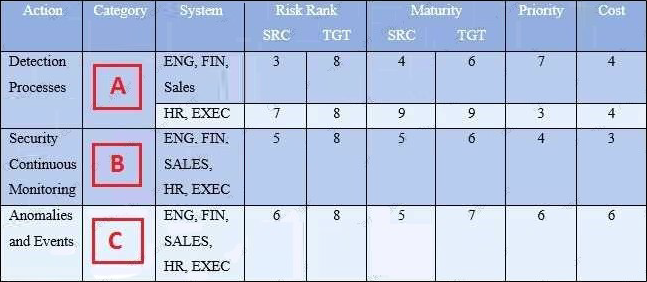
Your organization’s security team has been working with various business units to understand their business requirements, risk tolerance, and resources used to create a Framework Profile. Based on the Profile provided, what entries correspond to labels A, B, and C?

- A . Option A
- B . Option B
- C . Option C
What are the five categories that make up the Response function?
- A . Response Planning, Data Security, Communications, Analysis, and Mitigation
- B . Response Planning, Communications, Analysis, Mitigation, and Improvements
- C . Mitigation, Improvements, Maintenance, Response Planning, and Governance
- D . Awareness and Training, Improvements, Communications, Analysis, and Governance
During what activity does an organization identify and prioritize technical, organizational, procedural, administrative, and physical security weaknesses?
- A . Table top exercise
- B . Penetration testing
- C . Vulnerability assessment
- D . White box testing
Concerning a risk management strategy, what should the executive level be responsible for communicating?
- A . Risk mitigation
- B . Risk profile
- C . Risk tolerance
- D . Asset risk
