CompTIA CS0-003 Real Exam Questions
The questions for CS0-003 were last updated at Feb 18,2026.
- Exam Code: CS0-003
- Exam Name: CompTIA Cybersecurity Analyst (CySA+) Exam
- Certification Provider: CompTIA
- Latest update: Feb 18,2026
Which of the following will most likely ensure that mission-critical services are available in the event of an incident?
- A . Business continuity plan
- B . Vulnerability management plan
- C . Disaster recovery plan
- D . Asset management plan
A vulnerability management team is unable to patch all vulnerabilities found during their weekly scans.
Using the third-party scoring system described below, the team patches the most urgent vulnerabilities:
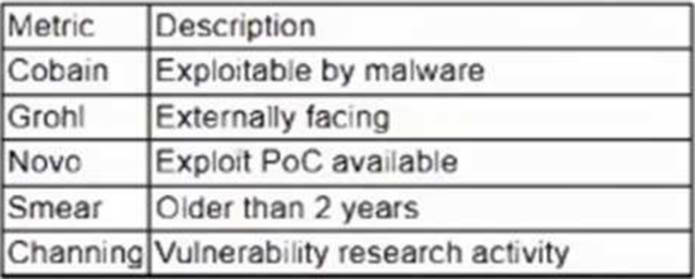
Additionally, the vulnerability management team feels that the metrics Smear and Channing are less important than the others, so these will be lower in priority.
Which of the following vulnerabilities should be patched first, given the above third-party scoring system?
- A . InLoud:
Cobain: Yes
Grohl: No
Novo: Yes
Smear: Yes
Channing: No - B . TSpirit:
Cobain: Yes
Grohl: Yes
Novo: Yes
Smear: No
Channing: No - C . ENameless:
Cobain: Yes
Grohl: No
Novo: Yes
Smear: No
Channing: No - D . PBleach:
Cobain: Yes
Grohl: No
Novo: No
Smear: No
Channing: Yes
A cybersecurity analyst is concerned about attacks that use advanced evasion techniques.
Which of the following would best mitigate such attacks?
- A . Keeping IPS rules up to date
- B . Installing a proxy server
- C . Applying network segmentation
- D . Updating the antivirus software
A security analyst is monitoring a company’s network traffic and finds ping requests going to accounting and human resources servers from a SQL server. Upon investigation, the analyst discovers a technician responded to potential network connectivity issues.
Which of the following is the best way for the security analyst to respond?
- A . Report this activity as a false positive, as the activity is legitimate.
- B . Isolate the system and begin a forensic investigation to determine what was compromised.
- C . Recommend network segmentation to the management team as a way to secure the various environments.
- D . Implement host-based firewalls on all systems to prevent ping sweeps in the future.
A company is in the process of implementing a vulnerability management program, and there are concerns about granting the security team access to sensitive data.
Which of the following scanning methods can be implemented to reduce the access to systems while providing the most accurate vulnerability scan results?
- A . Credentialed network scanning
- B . Passive scanning
- C . Agent-based scanning
- D . Dynamic scanning
A security analyst performs a weekly vulnerability scan on a network that has 240 devices and receives a report with 2.450 pages.
Which of the following would most likely decrease the number of false positives?
- A . Manual validation
- B . Penetration testing
- C . A known-environment assessment
- D . Credentialed scanning
A security analyst notices the following proxy log entries:
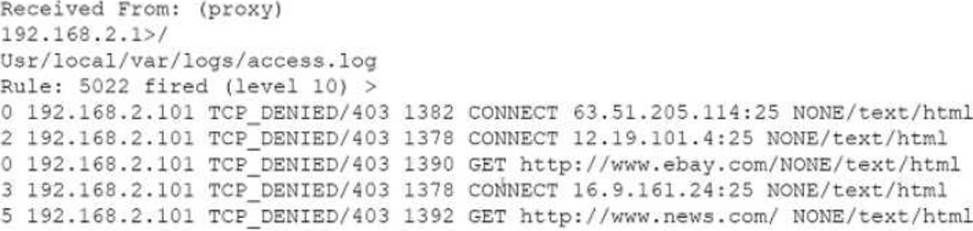
Which of the following is the user attempting to do based on the log entries?
- A . Use a DoS attack on external hosts.
- B . Exfiltrate data.
- C . Scan the network.
- D . Relay email.
An analyst finds that an IP address outside of the company network that is being used to run network and vulnerability scans across external-facing assets.
Which of the following steps of an attack framework is the analyst witnessing?
- A . Exploitation
- B . Reconnaissance
- C . Command and control
- D . Actions on objectives
A security analyst is performing an investigation involving multiple targeted Windows malware binaries. The analyst wants to gather intelligence without disclosing information to the attackers.
Which of the following actions would allow the analyst to achieve the objective?
- A . Upload the binary to an air gapped sandbox for analysis
- B . Send the binaries to the antivirus vendor
- C . Execute the binaries on an environment with internet connectivity
- D . Query the file hashes using VirusTotal
Which of the following is the first step that should be performed when establishing a disaster recovery plan?
- A . Agree on the goals and objectives of the plan
- B . Determine the site to be used during a disaster
C Demonstrate adherence to a standard disaster recovery process - C . Identity applications to be run during a disaster
