CompTIA CS0-003 Real Exam Questions
The questions for CS0-003 were last updated at Dec 28,2025.
- Exam Code: CS0-003
- Exam Name: CompTIA Cybersecurity Analyst (CySA+) Exam
- Certification Provider: CompTIA
- Latest update: Dec 28,2025
A security alert was triggered when an end user tried to access a website that is not allowed per organizational policy. Since the action is considered a terminable offense, the SOC analyst collects the authentication logs, web logs, and temporary files, reflecting the web searches from the user’s workstation, to build the case for the investigation.
Which of the following is the best way to ensure that the investigation complies with HR or privacy policies?
- A . Create a timeline of events detailinq the date stamps, user account hostname and IP information associated with the activities
- B . Ensure that the case details do not reflect any user-identifiable information Password protect the evidence and restrict access to personnel related to the investigation
- C . Create a code name for the investigation in the ticketing system so that all personnel with access will not be able to easily identity the case as an HR-related investigation
- D . Notify the SOC manager for awareness after confirmation that the activity was intentional
A security analyst discovers the company’s website is vulnerable to cross-site scripting.
Which of the following solutions will best remedy the vulnerability?
- A . Prepared statements
- B . Server-side input validation
- C . Client-side input encoding
- D . Disabled JavaScript filtering
Which of the following would help to minimize human engagement and aid in process improvement in security operations?
- A . OSSTMM
- B . SIEM
- C . SOAR
- D . QVVASP
A security analyst recently joined the team and is trying to determine which scripting language is being used in a production script to determine if it is malicious.
Given the following script:
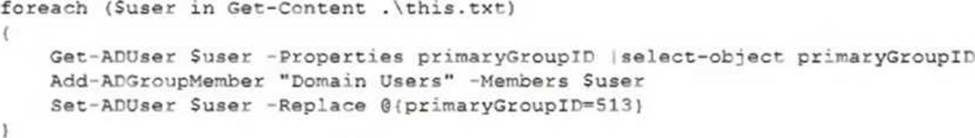
Which of the following scripting languages was used in the script?
- A . PowerShel
- B . Ruby
- C . Python
- D . Shell script
Which of the following phases of the Cyber Kill Chain involves the adversary attempting to establish communication with a successfully exploited target?
- A . Command and control
- B . Actions on objectives
- C . Exploitation
- D . Delivery
The Company shall prioritize patching of publicly available systems and services over patching of
internally available system.
According to the security policy, which of the following vulnerabilities should be the highest priority to patch?
A)
![]()
B)
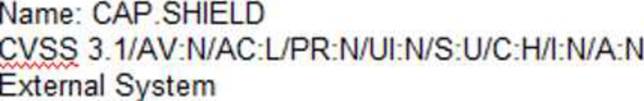
C)
![]()
D)
![]()
- A . Option A
- B . Option B
- C . Option C
- D . Option D
Which of the following describes how a CSIRT lead determines who should be communicated with and when during a security incident?
- A . The lead should review what is documented in the incident response policy or plan
- B . Management level members of the CSIRT should make that decision
- C . The lead has the authority to decide who to communicate with at any t me
- D . Subject matter experts on the team should communicate with others within the specified area of expertise
During an incident, an analyst needs to acquire evidence for later investigation.
Which of the following must be collected first in a computer system, related to its volatility level?
- A . Disk contents
- B . Backup data
- C . Temporary files
- D . Running processes
A security analyst is trying to identify anomalies on the network routing.
Which of the following functions can the analyst use on a shell script to achieve the objective most accurately?
- A . function x() { info=$(geoiplookup $1) && echo "$1 | $info" }
- B . function x() { info=$(ping -c 1 $1 | awk -F "/" ’END{print $5}’) && echo "$1 | $info" }
- C . function x() { info=$(dig $(dig -x $1 | grep PTR | tail -n 1 | awk -F ".in-addr" ’{print $1} ‘).origin.asn.cymru.com TXT +short) && echo "$1 | $info" }
- D . function x() { info=$(traceroute -m 40 $1 | awk ‘END{print $1}’) && echo "$1 | $info" }
During a company’s most recent incident, a vulnerability in custom software was exploited on an externally facing server by an APT.
The lessons-learned report noted the following:
• The development team used a new software language that was not supported by the security team’s automated assessment tools.
• During the deployment, the security assessment team was unfamiliar with the new language and struggled to evaluate the software during advanced testing. Therefore, the vulnerability was not detected.
• The current IPS did not have effective signatures and policies in place to detect and prevent
runtime attacks on the new application.
To allow this new technology to be deployed securely going forward, which of the following will BEST address these findings? (Choose two.)
- A . Train the security assessment team to evaluate the new language and verify that best practices for secure coding have been followed
- B . Work with the automated assessment-tool vendor to add support for the new language so these vulnerabilities are discovered automatically
- C . Contact the human resources department to hire new security team members who are already familiar with the new language
- D . Run the software on isolated systems so when they are compromised, the attacker cannot pivot to adjacent systems
- E . Instruct only the development team to document the remediation steps for this vulnerability
- F . Outsource development and hosting of the applications in the new language to a third-party vendor so the risk is transferred to that provider
