CompTIA CS0-003 Real Exam Questions
The questions for CS0-003 were last updated at Apr 01,2025.
- Exam Code: CS0-003
- Exam Name: CompTIA Cybersecurity Analyst (CySA+) Exam
- Certification Provider: CompTIA
- Latest update: Apr 01,2025
New employees in an organization have been consistently plugging in personal webcams despite the company policy prohibiting use of personal devices. The SOC manager discovers that new employees are not aware of the company policy.
Which of the following will the SOC manager most likely recommend to help ensure new employees are accountable for following the company policy?
- A . Human resources must email a copy of a user agreement to all new employees
- B . Supervisors must get verbal confirmation from new employees indicating they have read the user agreement
- C . All new employees must take a test about the company security policy during the cjitoardmg process
- D . All new employees must sign a user agreement to acknowledge the company security policy
A product manager is working with an analyst to design a new application that will perform as a data analytics platform and will be accessible via a web browser. The product manager suggests using a PaaS provider to host the application.
Which of the following is a security concern when using a PaaS solution?
- A . The use of infrastructure-as-code capabilities leads to an increased attack surface.
- B . Patching the underlying application server becomes the responsibility of the client.
- C . The application is unable to use encryption at the database level.
- D . Insecure application programming interfaces can lead to data compromise.
The steering committee for information security management annually reviews the security incident register for the organization to look for trends and systematic issues. The steering committee wants to rank the risks based on past incidents to improve the security program for next year.
Below is the incident register for the organization:
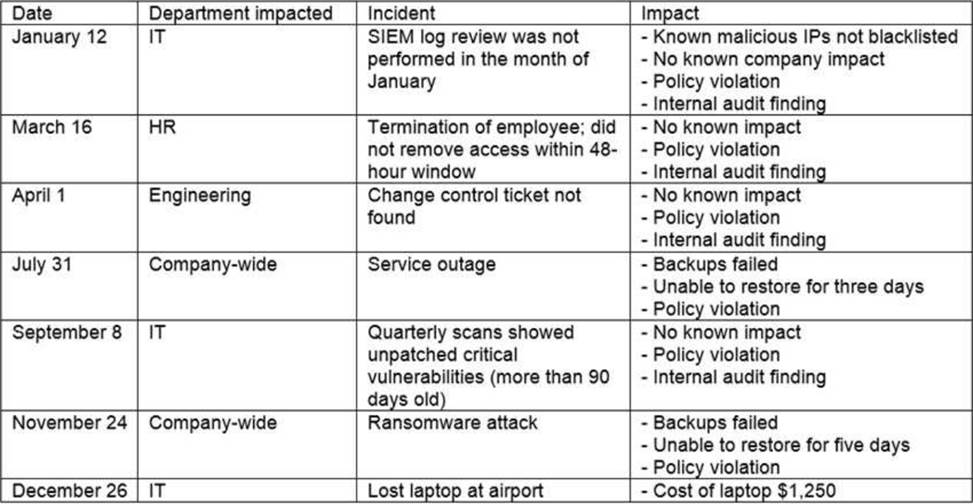
Which of the following should the organization consider investing in first due to the potential impact of availability?
- A . Hire a managed service provider to help with vulnerability management.
- B . Build a warm site in case of system outages.
- C . Invest in a failover and redundant system, as necessary.
- D . Hire additional staff for the IT department to assist with vulnerability management and log review.
A Chief Information Security Officer (CISO) is concerned about new privacy regulations that apply to the company. The CISO has tasked a security analyst with finding the proper control functions to verify that a user’s data is not altered without the user’s consent.
Which of the following would be an appropriate course of action?
- A . Automate the use of a hashing algorithm after verified users make changes to their data.
- B . Use encryption first and then hash the data at regular, defined times.
- C . Use a DLP product to monitor the data sets for unauthorized edits and changes.
- D . Replicate the data sets at regular intervals and continuously compare the copies for unauthorized changes.
A recent zero-day vulnerability is being actively exploited, requires no user interaction or privilege escalation, and has a significant impact to confidentiality and integrity but not to availability.
Which of the following CVE metrics would be most accurate for this zero-day threat?
- A . CVSS: 31/AV: N/AC: L/PR: N/UI: N/S: U/C: H/1: K/A: L
- B . CVSS:31/AV:K/AC:L/PR:H/UI:R/S:C/C:H/I:H/A:L
- C . CVSS:31/AV:N/AC:L/PR:N/UI:H/S:U/C:L/I:N/A:H
- D . CVSS:31/AV:L/AC:L/PR:R/UI:R/S:U/C:H/I:L/A:H
An incident response team receives an alert to start an investigation of an internet outage. The outage is preventing all users in multiple locations from accessing external SaaS resources. The team determines the organization was impacted by a DDoS attack.
Which of the following logs should the team review first?
- A . CDN
- B . Vulnerability scanner
- C . DNS
- D . Web server
A SOC manager receives a phone call from an upset customer. The customer received a vulnerability report two hours ago: but the report did not have a follow-up remediation response from an analyst.
Which of the following documents should the SOC manager review to ensure the team is meeting the appropriate contractual obligations for the customer?
- A . SLA
- B . MOU
- C . NDA
- D . Limitation of liability
As a proactive threat-hunting technique, hunters must develop situational cases based on likely attack scenarios derived from the available threat intelligence information. After forming the basis of the scenario, which of the following may the threat hunter construct to establish a framework for threat assessment?
- A . Critical asset list
- B . Threat vector
- C . Attack profile
- D . Hypothesis
An incident response analyst notices multiple emails traversing the network that target only the administrators of the company. The email contains a concealed URL that leads to an unknown website in another country.
Which of the following best describes what is happening? (Choose two.)
- A . Beaconinq
- B . Domain Name System hijacking
- C . Social engineering attack
- D . On-path attack
- E . Obfuscated links
- F . Address Resolution Protocol poisoning
A security analyst wants to capture large amounts of network data that will be analyzed at a later time. The packet capture does not need to be in a format that is readable by humans, since it will be put into a binary file called "packetCapture." The capture must be as efficient as possible, and the analyst wants to minimize the likelihood that packets will be missed.
Which of the following commands will best accomplish the analyst’s objectives?
- A . tcpdump -w packetCapture
- B . tcpdump -a packetCapture
- C . tcpdump -n packetCapture
- D . nmap -v > packetCapture
- E . nmap -oA > packetCapture
