CompTIA CAS-004 Real Exam Questions
The questions for CAS-004 were last updated at Jan 23,2026.
- Exam Code: CAS-004
- Exam Name: CompTIA Advanced Security Practitioner (CASP+) Exam
- Certification Provider: CompTIA
- Latest update: Jan 23,2026
After a security incident, a network security engineer discovers that a portion of the company’s sensitive external traffic has been redirected through a secondary ISP that is not normally used.
Which of the following would BEST secure the routes while allowing the network to function in the event of a single provider failure?
- A . Disable BGP and implement a single static route for each internal network.
- B . Implement a BGP route reflector.
- C . Implement an inbound BGP prefix list.
- D . Disable BGP and implement OSPF.
A developer wants to maintain integrity to each module of a program and ensure the code cannot be altered by malicious users.
Which of the following would be BEST for the developer to perform? (Choose two.)
- A . Utilize code signing by a trusted third party.
- B . Implement certificate-based authentication.
- C . Verify MD5 hashes.
- D . Compress the program with a password.
- E . Encrypt with 3DES.
- F . Make the DACL read-only.
A company is preparing to deploy a global service.
Which of the following must the company do to ensure GDPR compliance? (Choose two.)
- A . Inform users regarding what data is stored.
- B . Provide opt-in/out for marketing messages.
- C . Provide data deletion capabilities.
- D . Provide optional data encryption.
- E . Grant data access to third parties.
- F . Provide alternative authentication techniques.
A security is assisting the marketing department with ensuring the security of the organization’s social media platforms.
The two main concerns are:
The Chief marketing officer (CMO) email is being used department wide as the username
The password has been shared within the department
Which of the following controls would be BEST for the analyst to recommend?
- A . Configure MFA for all users to decrease their reliance on other authentication.
- B . Have periodic, scheduled reviews to determine which OAuth configuration are set for each media platform.
- C . Create multiple social media accounts for all marketing user to separate their actions.
- D . Ensue the password being shared is sufficiently and not written down anywhere.
A company is looking to fortify its cybersecurity defenses and is focusing on its network infrastructure. The solution cannot affect the availability of the company’s services to ensure false positives do not drop legitimate traffic.
Which of the following would satisfy the requirement?
- A . NIDS
- B . NIPS
- C . WAF
- D . Reverse proxy
An organization recently started processing, transmitting, and storing its customers’ credit card information. Within a week of doing so, the organization suffered a massive breach that resulted in the exposure of the customers’ information.
Which of the following provides the BEST guidance for protecting such information while it is at rest and in transit?
- A . NIST
- B . GDPR
- C . PCI DSS
- D . ISO
A company that uses AD is migrating services from LDAP to secure LDAP. During the pilot phase, services are not connecting properly to secure LDAP.
Block is an except of output from the troubleshooting session:
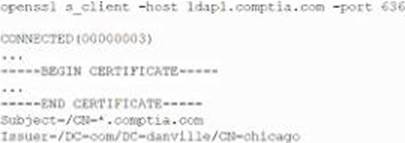
Which of the following BEST explains why secure LDAP is not working? (Select TWO.)
- A . The clients may not trust idapt by default.
- B . The secure LDAP service is not started, so no connections can be made.
- C . Danvills.com is under a DDoS-inator attack and cannot respond to OCSP requests.
- D . Secure LDAP should be running on UDP rather than TCP.
- E . The company is using the wrong port. It should be using port 389 for secure LDAP.
- F . Secure LDAP does not support wildcard certificates.
- G . The clients may not trust Chicago by default.
A company has decided to purchase a license for software that is used to operate a mission-critical process. The third-party developer is new to the industry but is delivering what the company needs at this time.
Which of the following BEST describes the reason why utilizing a source code escrow will reduce the operational risk to the company if the third party stops supporting the application?
- A . The company will have access to the latest version to continue development.
- B . The company will be able to force the third-party developer to continue support.
- C . The company will be able to manage the third-party developer’s development process.
- D . The company will be paid by the third-party developer to hire a new development team.
A security analyst is concerned that a malicious piece of code was downloaded on a Linux system. After some research, the analyst determines that the suspected piece of code is performing a lot of input/output (I/O) on the disk drive.
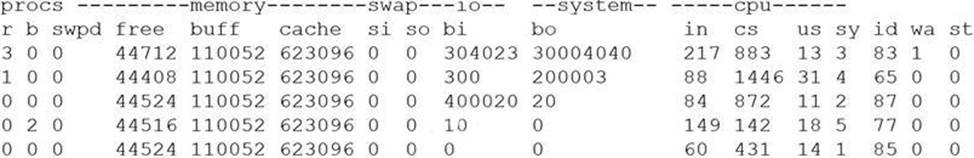
Based on the output above, from which of the following process IDs can the analyst begin an investigation?
- A . 65
- B . 77
- C . 83
- D . 87
Despite the fact that ten new API servers were added, the load across servers was heavy at peak times.
Which of the following infrastructure design changes would be BEST for the organization to implement to avoid these issues in the future?
- A . Serve static content via distributed CDNs, create a read replica of the central database and pull reports from there, and auto-scale API servers based on performance.
- B . Increase the bandwidth for the server that delivers images, use a CDN, change the database to a non-relational database, and split the ten API servers across two load balancers.
- C . Serve images from an object storage bucket with infrequent read times, replicate the database across different regions, and dynamically create API servers based on load.
- D . Serve static-content object storage across different regions, increase the instance size on the managed relational database, and distribute the ten API servers across multiple regions.
