CompTIA CAS-004 Real Exam Questions
The questions for CAS-004 were last updated at Apr 01,2025.
- Exam Code: CAS-004
- Exam Name: CompTIA Advanced Security Practitioner (CASP+) Exam
- Certification Provider: CompTIA
- Latest update: Apr 01,2025
The Chief information Officer (CIO) of a large bank, which uses multiple third-party organizations to deliver a service, is concerned about the handling and security of customer data by the parties.
Which of the following should be implemented to BEST manage the risk?
- A . Establish a review committee that assesses the importance of suppliers and ranks them according to contract renewals. At the time of contract renewal, incorporate designs and operational controls into the contracts and a right-to-audit clause. Regularly assess the supplier’s post-contract renewal with a dedicated risk management team.
- B . Establish a team using members from first line risk, the business unit, and vendor management to assess only design security controls of all suppliers. Store findings from the reviews in a database for all other business units and risk teams to reference.
- C . Establish an audit program that regularly reviews all suppliers regardless of the data they access, how they access the data, and the type of data, Review all design and operational controls based on best practice standard and report the finding back to upper management.
- D . Establish a governance program that rates suppliers based on their access to data, the type of data, and how they access the data Assign key controls that are reviewed and managed based on the supplier’s rating. Report finding units that rely on the suppliers and the various risk teams.
The Chief information Officer (CIO) of a large bank, which uses multiple third-party organizations to deliver a service, is concerned about the handling and security of customer data by the parties.
Which of the following should be implemented to BEST manage the risk?
- A . Establish a review committee that assesses the importance of suppliers and ranks them according to contract renewals. At the time of contract renewal, incorporate designs and operational controls into the contracts and a right-to-audit clause. Regularly assess the supplier’s post-contract renewal with a dedicated risk management team.
- B . Establish a team using members from first line risk, the business unit, and vendor management to assess only design security controls of all suppliers. Store findings from the reviews in a database for all other business units and risk teams to reference.
- C . Establish an audit program that regularly reviews all suppliers regardless of the data they access, how they access the data, and the type of data, Review all design and operational controls based on best practice standard and report the finding back to upper management.
- D . Establish a governance program that rates suppliers based on their access to data, the type of data, and how they access the data Assign key controls that are reviewed and managed based on the supplier’s rating. Report finding units that rely on the suppliers and the various risk teams.
An e-commerce company is running a web server on premises, and the resource utilization is usually less than 30%. During the last two holiday seasons, the server experienced performance issues because of too many connections, and several customers were not able to finalize purchase orders. The company is looking to change the server configuration to avoid this kind of performance issue.
Which of the following is the MOST cost-effective solution?
- A . Move the server to a cloud provider.
- B . Change the operating system.
- C . Buy a new server and create an active-active cluster.
- D . Upgrade the server with a new one.
A high-severity vulnerability was found on a web application and introduced to the enterprise. The vulnerability could allow an unauthorized user to utilize an open-source library to view privileged user information. The enterprise is unwilling to accept the risk, but the developers cannot fix the issue right away.
Which of the following should be implemented to reduce the risk to an acceptable level until the issue can be fixed?
- A . Scan the code with a static code analyzer, change privileged user passwords, and provide security training.
- B . Change privileged usernames, review the OS logs, and deploy hardware tokens.
- C . Implement MFA, review the application logs, and deploy a WAF.
- D . Deploy a VPN, configure an official open-source library repository, and perform a full application review for vulnerabilities.
An organization is preparing to migrate its production environment systems from an on-premises environment to a cloud service. The lead security architect is concerned that the organization’s current methods for addressing risk may not be possible in the cloud environment.
Which of the following BEST describes the reason why traditional methods of addressing risk may not be possible in the cloud?
- A . Migrating operations assumes the acceptance of all risk.
- B . Cloud providers are unable to avoid risk.
- C . Specific risks cannot be transferred to the cloud provider.
- D . Risks to data in the cloud cannot be mitigated.
A company undergoing digital transformation is reviewing the resiliency of a CSP and is concerned about meeting SLA requirements in the event of a CSP incident.
Which of the following would be BEST to proceed with the transformation?
- A . An on-premises solution as a backup
- B . A load balancer with a round-robin configuration
- C . A multicloud provider solution
- D . An active-active solution within the same tenant
A company is migrating from company-owned phones to a BYOD strategy for mobile devices. The pilot program will start with the executive management team and be rolled out to the rest of the staff in phases. The company’s Chief Financial Officer loses a phone multiple times a year.
Which of the following will MOST likely secure the data on the lost device?
- A . Require a VPN to be active to access company data.
- B . Set up different profiles based on the person’s risk.
- C . Remotely wipe the device.
- D . Require MFA to access company applications.
All staff at a company have started working remotely due to a global pandemic. To transition to remote work, the company has migrated to SaaS collaboration tools.
The human resources department wants to use these tools to process sensitive information but is concerned the data could be:
Leaked to the media via printing of the documents
Sent to a personal email address
Accessed and viewed by systems administrators
Uploaded to a file storage site
Which of the following would mitigate the department’s concerns?
- A . Data loss detection, reverse proxy, EDR, and PGP
- B . VDI, proxy, CASB, and DRM
- C . Watermarking, forward proxy, DLP, and MFA
- D . Proxy, secure VPN, endpoint encryption, and AV
Device event logs sources from MDM software as follows:
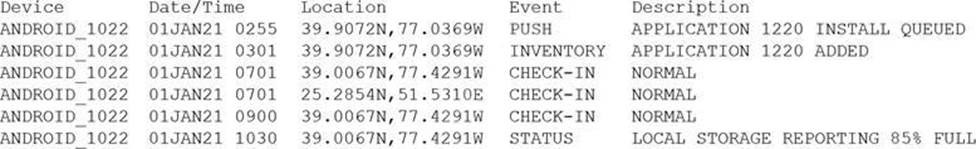
Which of the following security concerns and response actions would BEST address the risks posed by the device in the logs?
- A . Malicious installation of an application; change the MDM configuration to remove application ID 1220.
- B . Resource leak; recover the device for analysis and clean up the local storage.
- C . Impossible travel; disable the device’s account and access while investigating.
- D . Falsified status reporting; remotely wipe the device.
Which of the following are risks associated with vendor lock-in? (Choose two.)
- A . The client can seamlessly move data.
- B . The vendor can change product offerings.
- C . The client receives a sufficient level of service.
- D . The client experiences decreased quality of service.
- E . The client can leverage a multicloud approach.
- F . The client experiences increased interoperability.
