Microsoft AZ-500 Real Exam Questions
The questions for AZ-500 were last updated at Apr 16,2025.
- Exam Code: AZ-500
- Exam Name: Microsoft Azure Security Technologies
- Certification Provider: Microsoft
- Latest update: Apr 16,2025
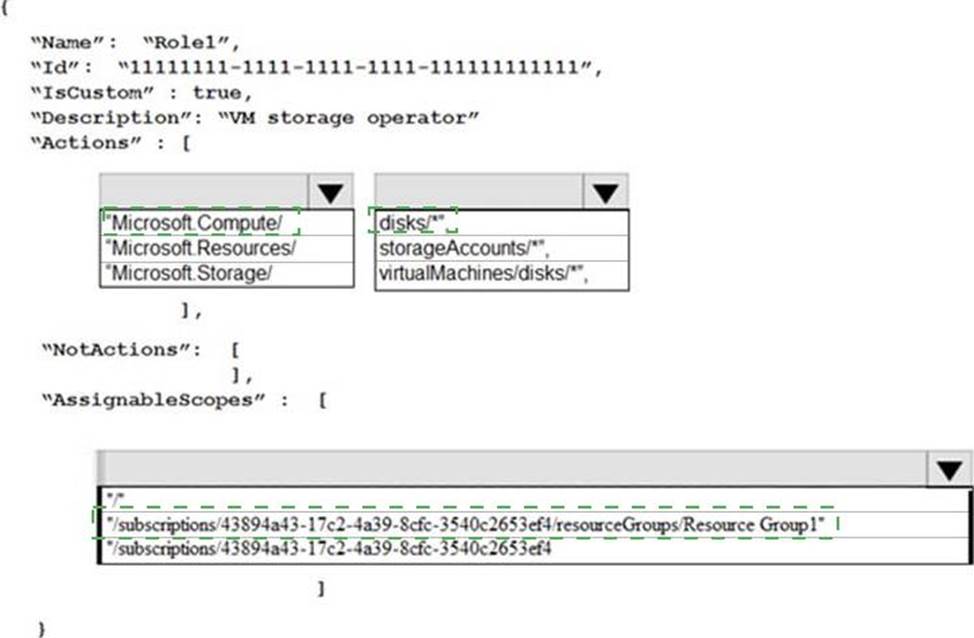
HOTSPOT
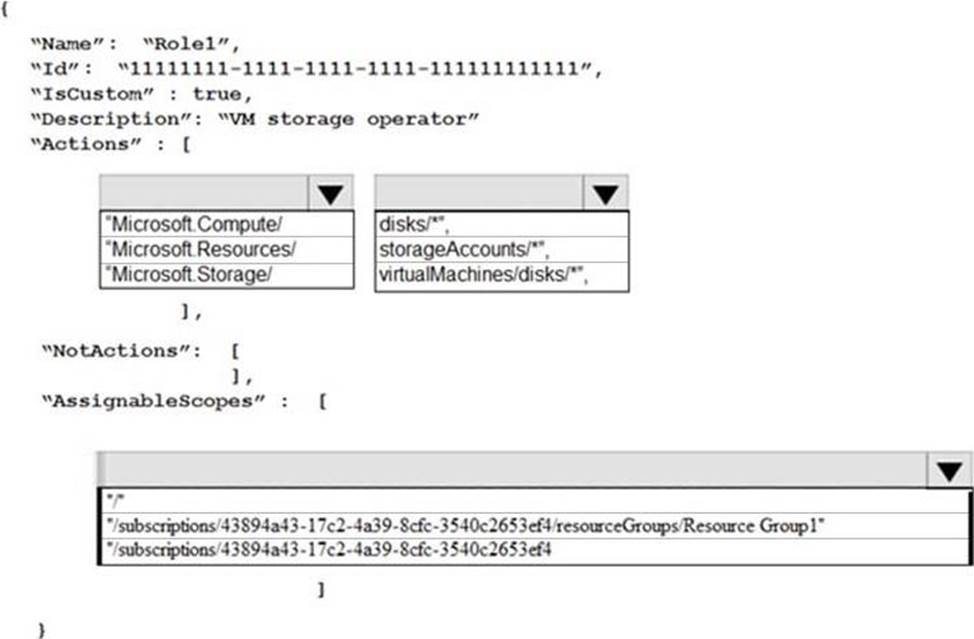
You need to create Role1 to meet the platform protection requirements.
How should you complete the role definition of Role1? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You plan to use Azure Resource Manager templates to perform multiple deployments of identically configured Azure virtual machines. The password for the administrator account of each deployment is stored as a secret in different Azure key vaults.
You need to identify a method to dynamically construct a resource ID that will designate the key vault containing the appropriate secret during each deployment. The name of the key vault and the name of the
secret will be provided as inline parameters.
What should you use to construct the resource ID?
- A . a key vault access policy
- B . a linked template
- C . a parameters file
- D . an automation account
You have a hybrid configuration of Azure Active Directory (Azure AD). You have an Azure SQL Database instance that is configured to support Azure AD authentication.
Database developers must connect to the database instance and authenticate by using their on-premises
Active Directory account.
You need to ensure that developers can connect to the instance by using Microsoft SQL Server Management Studio. The solution must minimize authentication prompts.
Which authentication method should you recommend?
- A . Active Directory – Password
- B . Active Directory – Universal with MFA support
- C . SQL Server Authentication
- D . Active Directory – Integrated
You have a hybrid configuration of Azure Active Directory (Azure AD). You have an Azure SQL Database instance that is configured to support Azure AD authentication.
Database developers must connect to the database instance and authenticate by using their on-premises
Active Directory account.
You need to ensure that developers can connect to the instance by using Microsoft SQL Server Management Studio. The solution must minimize authentication prompts.
Which authentication method should you recommend?
- A . Active Directory – Password
- B . Active Directory – Universal with MFA support
- C . SQL Server Authentication
- D . Active Directory – Integrated
You need to ensure that users can access VM0. The solution must meet the platform protection requirements.
What should you do?
- A . Move VM0 to Subnet1.
- B . On Firewall, configure a network traffic filtering rule.
- C . Assign RT1 to AzureFirewallSubnet.
- D . On Firewall, configure a DNAT rule.
You need to ensure that users can access VM0. The solution must meet the platform protection requirements.
What should you do?
- A . Move VM0 to Subnet1.
- B . On Firewall, configure a network traffic filtering rule.
- C . Assign RT1 to AzureFirewallSubnet.
- D . On Firewall, configure a DNAT rule.
You need to ensure that you can meet the security operations requirements.
What should you do first?
- A . Turn on Auto Provisioning in Security Center.
- B . Integrate Security Center and Microsoft Cloud App Security.
- C . Upgrade the pricing tier of Security Center to Standard.
- D . Modify the Security Center workspace configuration.
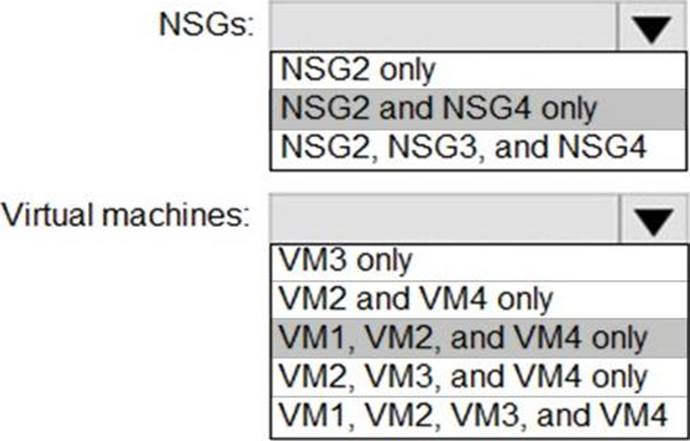
HOTSPOT
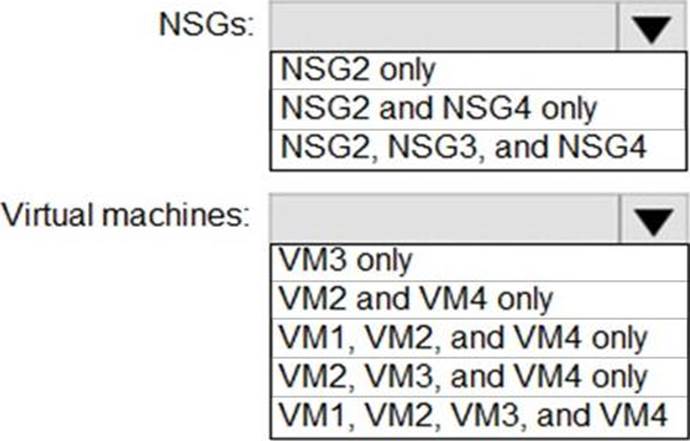
You implement the planned changes for ASG1 and ASG2.
In which NSGs can you use ASG1. and the network interfaces of which virtual machines can you assign to ASG2?
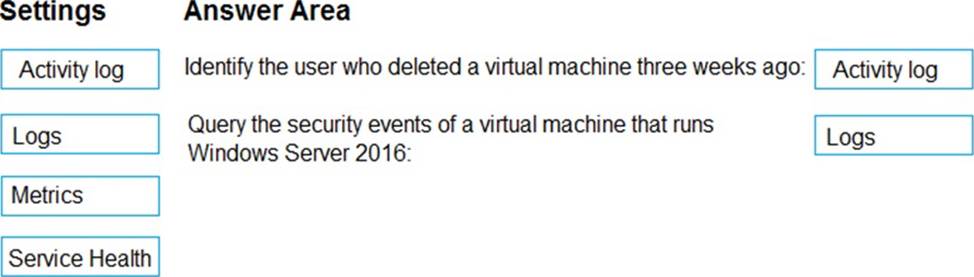
DRAG DROP
You have an Azure subscription that contains 100 virtual machines. Azure Diagnostics is enabled on all the virtual machines.
You are planning the monitoring of Azure services in the subscription.
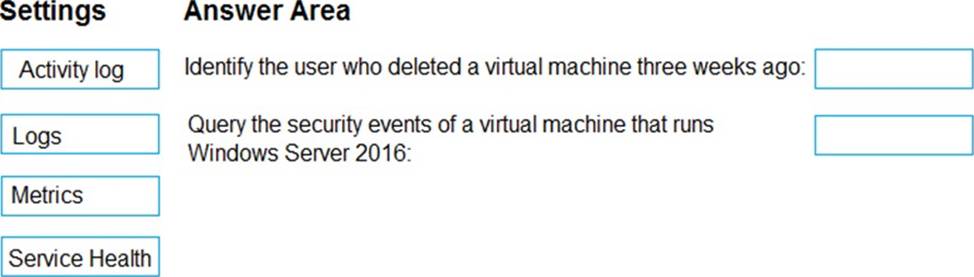
You need to retrieve the following details:
– Identify the user who deleted a virtual machine three weeks ago.
– Query the security events of a virtual machine that runs Windows Server 2016.
What should you use in Azure Monitor? To answer, drag the appropriate configuration settings to the correct details. Each configuration setting may be used once, more than once, or not at all.
You may need to drag the split bar between panes or scroll to view content. NOTE: Each correct selection is worth one point.
HOTSPOT
You have an Azure subscription named Sub1.
You create a virtual network that contains one subnet.
On the subnet, you provision the virtual machines shown in the following table.
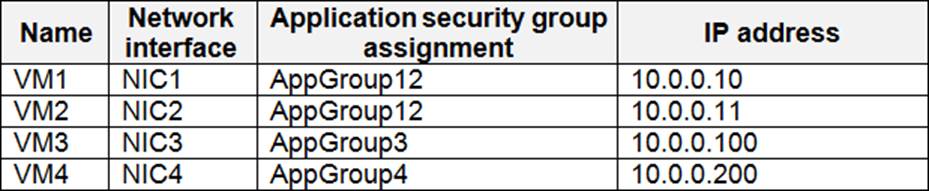
Currently, you have not provisioned any network security groups (NSGs).
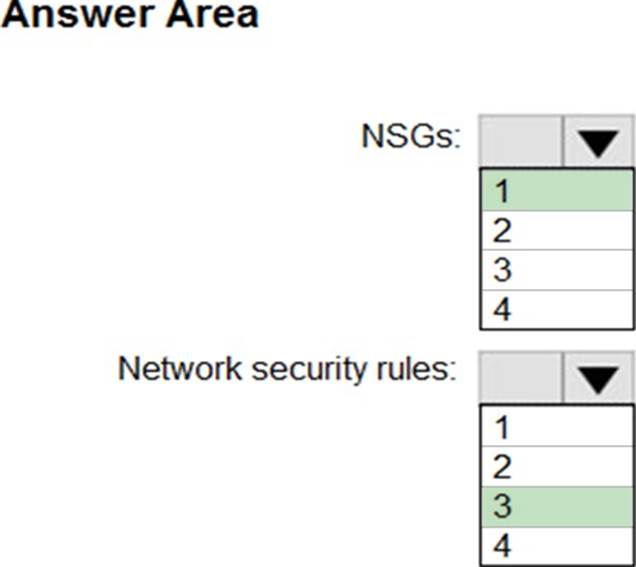
You need to implement network security to meet the following requirements:
– Allow traffic to VM4 from VM3 only.
– Allow traffic from the Internet to VM1 and VM2 only.
– Minimize the number of NSGs and network security rules.
How many NSGs and network security rules should you create? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.