Cisco 350-401 Real Exam Questions
The questions for 350-401 were last updated at Apr 23,2025.
- Exam Code: 350-401
- Exam Name: Implementing and Operating Cisco Enterprise Network Core Technologies (ENCOR)
- Certification Provider: Cisco
- Latest update: Apr 23,2025
Which command set configures RSPAN to capture outgoing traffic from VLAN 3 on interface GigabitEthernet 0/3 while ignoring other VLAN traffic on the same interface?
- A . monitor session 2 source interface gigabitethernet0/3 tx
monitor session 2 filter vlan 3 - B . monitor session 2 source interface gigabitethernet0/3 tx
monitor session 2 filter vlan 1- 2, 4 – 4094 - C . monitor session 2 source interface gigabitethernet0/3 rx
monitor session 2 filter vlan 3 - D . monitor session 2 source interface gigabitethernet0/3 rx
monitor session 2 filter vlan 1 – 2, 4 – 4094
Refer the exhibit.
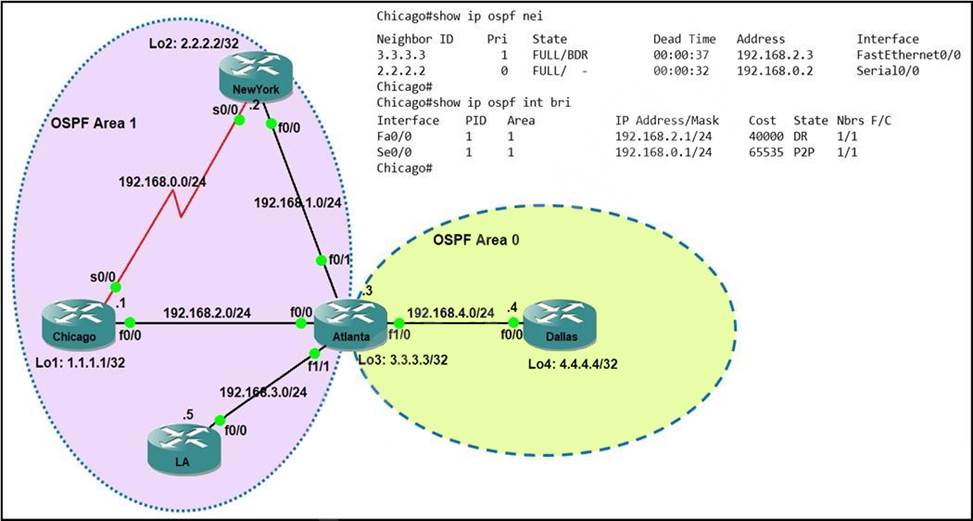
Which router is the designated router on the segment 192.168.0.0/24?
- A . This segment has no designated router because it is a nonbroadcast network type.
- B . This segment has no designated router because it is a p2p network type.
- C . Router Chicago because it has a lower router ID
- D . Router NewYork because it has a higher router ID
At which Layer does Cisco DNA Center support REST controls?
- A . EEM applets or scripts
- B . Session layer
- C . YMAL output from responses to API calls
- D . Northbound APIs
What is used to perform OoS packet classification?
- A . the Options field in the Layer 3 header
- B . the Type field in the Layer 2 frame
- C . the Flags field in the Layer 3 header
- D . the TOS field in the Layer 3 header
What is a benefit of data modeling languages like YANG?
- A . They enable programmers to change or write their own application within the device operating system.
- B . They create more secure and efficient SNMP OIDs.
- C . They make the CLI simpler and more efficient.
- D . They provide a standardized data structure, which results in configuration scalability and consistency.
Refer to the exhibit.
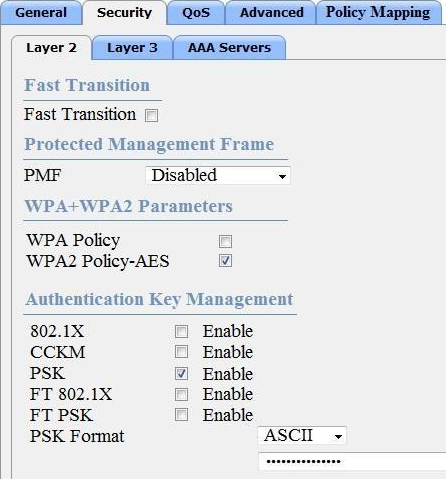
Based on the configuration in this WLAN security setting.
Which method can a client use to authenticate to the network?
- A . text string
- B . username and password
- C . certificate
- D . RADIUS token
Refer to the exhibit.
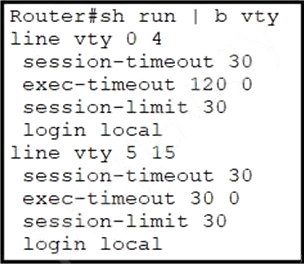
Security policy requires all idle-exec sessions to be terminated in 600 seconds.
Which configuration achieves this goal?
- A . line vty 0 15
absolute-timeout 600 - B . line vty 0 15
exec-timeout - C . line vty 01 5
exec-timeout 10 0 - D . line vty 0 4
exec-timeout 600
Which outbound access list, applied to the WAN interface of a router, permits all traffic except for http traffic sourced from the workstation with IP address 10.10.10.1?
- A . ip access-list extended 100
deny tcp host 10.10.10.1 any eq 80
permit ip any any - B . ip access-list extended 200
deny tcp host 10.10.10.1 eq 80 any
permit ip any any - C . ip access-list extended NO_HTTP
deny tcp host 10.10.10.1 any eq 80 - D . ip access-list extended 10
deny tcp host 10.10.10.1 any eq 80
permit ip any any
Refer to the exhibit.
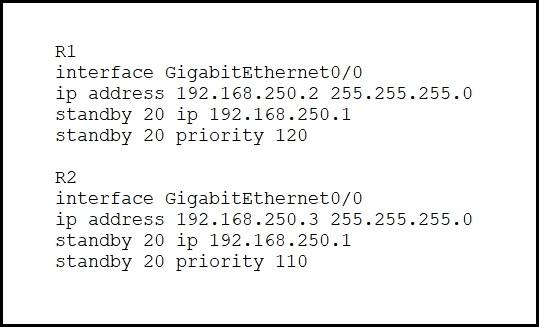
What are two effects of this configuration? (Choose two.)
- A . R1 becomes the active router.
- B . R1 becomes the standby router.
- C . If R2 goes down, R1 becomes active but reverts to standby when R2 comes back online.
- D . If R1 goes down. R2 becomes active and remains the active device when R1 comes back online.
- E . If R1 goes down, R2 becomes active but reverts to standby when R1 comes back online.
What are two differences between the RIB and the FIB? (Choose two.)
- A . The FIB is derived from the data plane, and the RIB is derived from the FIB.
- B . The RIB is a database of routing prefixes, and the FIB is the Information used to choose the egress interface for each packet.
- C . FIB is a database of routing prefixes, and the RIB is the information used to choose the egress interface for each packet.
- D . The FIB is derived from the control plane, and the RIB is derived from the FIB.
- E . The RIB is derived from the control plane, and the FIB is derived from the RIB.
