Cisco 300-810 Real Exam Questions
The questions for 300-810 were last updated at Mar 31,2025.
- Exam Code: 300-810
- Exam Name: Implementing Cisco Collaboration Applications (CLICA)
- Certification Provider: Cisco
- Latest update: Mar 31,2025
An organization has two Cisco IM and Presence clusters: one in the Americas and one in EMEAR. Both clusters connect via an intercluster peer. Each Cisco IM and Presence cluster has four nodes logically divided into two subclusters with high availability enabled with its local peers.
When the Cisco IM and Presence publisher node in the Americas fails, to where are the users failed over?
- A . Cisco IM and Presence publisher in EMEAR. in the different logical group
- B . Cisco IM and Presence subscriber in the Americas, in the different logical group
- C . Cisco IM and Presence subscriber in EMEAR. in the same logical group with IM and Presence publisher
- D . Cisco IM and Presence subscriber in the Americas, in the same logical group with IM and Presence publisher
Refer to the exhibit.
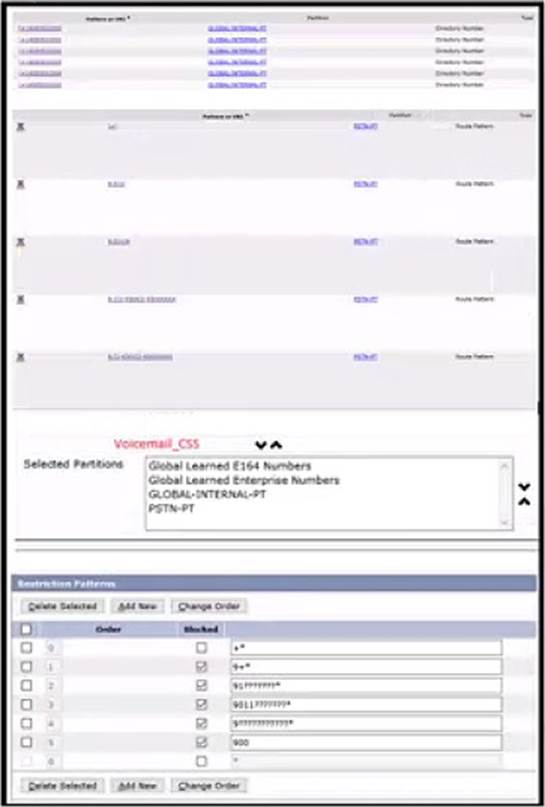
Cisco UCM is integrated with Cisco Unity connection via a SIP truck and is configured using a globalized dial plan (directory number are configured with “*”).
Using cisco best practices, which implementation allows call transfers to internal directory numbers but not to PSTN numbers?
- A . remove PSTN-PT from voicemail_CSS
- B . change the order of partitions to put GLOBAL-INERNAL-PT first in Voicemail_CSS
- C . create a BLOCK-PSTN-PT partition and add it to Voicemail_CSS
- D . block pattern +* in the Cisco Unity restriction table
What are two characteristics of HTTPS networking for Cisco Unity Connection? (Choose two)
- A . HTTPS single-site networks are joined via an intersite link
- B . HTTPS networking uses a ring topology
- C . HTTPS networking supports a maximum of 25 locations
- D . HTTPS networking uses the SMTP protocol
- E . HTTPS networking supports multisite networks
An administrator must Implement toll-fraud prevention on Cisco Unity Connection by using restricted tables.
Which action accomplishes this task?
- A . Block all numbers that start with 999*.
- B . Allow calls to international operators and conference rooms only.
- C . Permit calls only to specific domestic long-distance area codes.
- D . Allow calls to the international operator only.
An engineer is configuring Cisco Unified IM and Presence on-premises SIP Federation. The IM and Presence Service node cannot find the external domain using DNS SRV. Assuming the DNS SRV configuration is Correct.
What should the engineer configure next to resolve this issue?
- A . A static route that points to the internal interface of the external domain.
- B . A static route that points to the external Interface of the external domain.
- C . A static route on the external domain points to the external interface.
- D . A dynamic route on the external domain that points to the internal Interface.
An engineer is configuring XMPP federation on the Cisco IM and Presence server and has changed the security settings to TLS Optional on one node in the cluster.
What is the next step in the configuration process?
- A . Start the Cisco DB Replicator
- B . Start the Cisco Replication Watcher.
- C . Restart the Cisco XCP Router.
- D . Restart the Cisco Presence Engine
Which DNS record is used for on-premises service by Jabber clients?
- A . _collab-edge._tcp.<domain> SRV record
- B . _cisco-uds._tls.<domain> SRV record
- C . _cisco-uds._tcp.<domain> SRV record
- D . <tftp server FQDN> A record
An engineer must verify that the DNS SRV entries that are configured have the correct Information.
How Is this configuration completed via a Windows machine?
- A . Go to Windows Explorer and type nslookup. Set the type=internet, and then enter the SRV record.
- B . Go to the command prompt and type dnslookup. Set the type=sip. and then enter the SRV record.
- C . Go to Internet Explorer and type nslookup. Set the type=srv, and then enter the SRV record.
- D . Go to the command prompt and type nslookup. Set the type=srv, and then enter the SRV record.
Which description of an IdP server is true?
- A . authenticates user credentials
- B . provides user authorization
- C . is an authentication request that is generated by a Cisco Unified Communications application
- D . consists of pieces of security information that are transferred to the service provider for user authentication
An engineer is importing users into Cisco Unity Connection using AXL and discovers that some users are not listed in the import view.
Which action should be taken to resolve this issue?
- A . Configure the user primary extension to their directory number.
- B . Configure the user digest credentials to match the user password.
- C . Configure the user access control group assignment to Standard CTI Enabled.
- D . Configure the username and password in LDAP.
