Cisco 200-201 Real Exam Questions
The questions for 200-201 were last updated at Dec 24,2025.
- Exam Code: 200-201
- Exam Name: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
- Certification Provider: Cisco
- Latest update: Dec 24,2025
Refer to the exhibit.
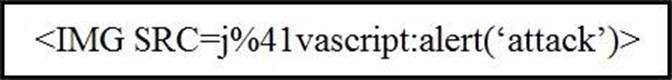
Which kind of attack method is depicted in this string?
- A . cross-site scripting
- B . man-in-the-middle
- C . SQL injection
- D . denial of service
Refer to the exhibit.
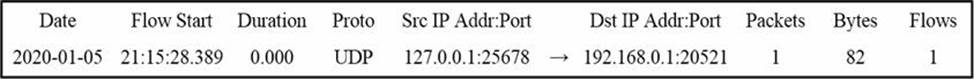
Which type of log is displayed?
- A . proxy
- B . NetFlow
- C . IDS
- D . sys
Refer to the exhibit.
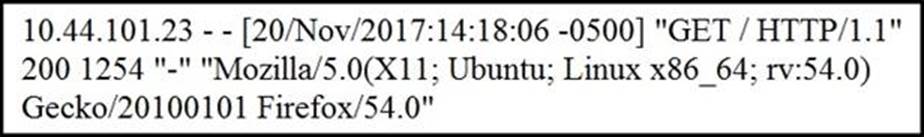
What does the message indicate?
- A . an access attempt was made from the Mosaic web browser
- B . a successful access attempt was made to retrieve the password file
- C . a successful access attempt was made to retrieve the root of the website
- D . a denied access attempt was made to retrieve the password file
Which security technology guarantees the integrity and authenticity of all messages transferred to and from a web application?
- A . Hypertext Transfer Protocol
- B . SSL Certificate
- C . Tunneling
- D . VPN
What is the practice of giving an employee access to only the resources needed to accomplish their job?
- A . principle of least privilege
- B . organizational separation
- C . separation of duties
- D . need to know principle
What are two differences in how tampered and untampered disk images affect a security incident? (Choose two.)
- A . Untampered images are used in the security investigation process
- B . Tampered images are used in the security investigation process
- C . The image is tampered if the stored hash and the computed hash match
- D . Tampered images are used in the incident recovery process
- E . The image is untampered if the stored hash and the computed hash match
AE
Explanation:
Cert Guide by Omar Santos, Chapter 9 – Introduction to digital Forensics. "When you collect evidence, you must protect its integrity. This involves making sure that nothing is added to the evidence and that nothing is deleted or destroyed (this is known as evidence preservation)."
Which event is user interaction?
- A . gaining root access
- B . executing remote code
- C . reading and writing file permission
- D . opening a malicious file
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
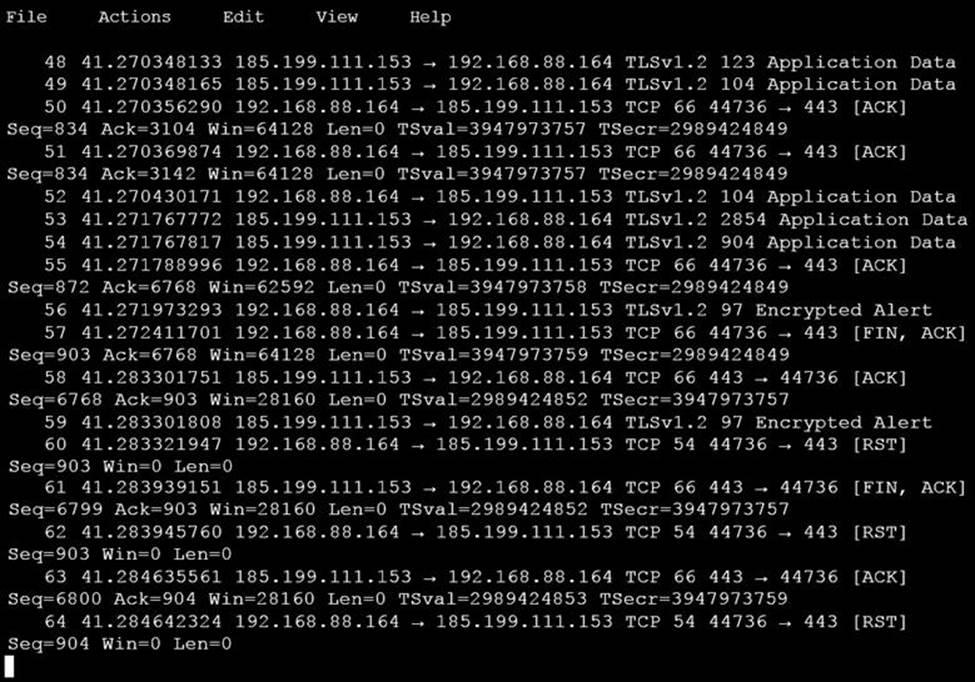
Which obfuscation technique is the attacker using?
- A . Base64 encoding
- B . TLS encryption
- C . SHA-256 hashing
- D . ROT13 encryption
B
Explanation:
ROT13 is considered weak encryption and is not used with TLS (HTTPS:443). Source: https://en.wikipedia.org/wiki/ROT13
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor.
Which type of evidence is this?
- A . best evidence
- B . prima facie evidence
- C . indirect evidence
- D . physical evidence
C
Explanation:
There are three general types of evidence:
–> Best evidence: can be presented in court in the original form (for example, an exact copy of a hard disk drive).
–> Corroborating evidence: tends to support a theory or an assumption deduced by some initial evidence. This corroborating evidence confirms the proposition.
–> Indirect or circumstantial evidence: extrapolation to a conclusion of fact (such as fingerprints, DNA evidence, and so on).
Refer to the exhibit.
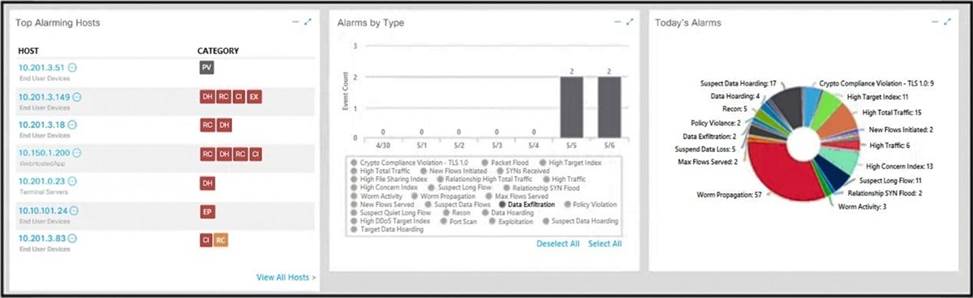
What is the potential threat identified in this Stealth watch dashboard?
- A . A policy violation is active for host 10.10.101.24.
- B . A host on the network is sending a DDoS attack to another inside host.
- C . There are two active data exfiltration alerts.
- D . A policy violation is active for host 10.201.3.149.
