Cisco 200-201 Real Exam Questions
The questions for 200-201 were last updated at Apr 09,2025.
- Exam Code: 200-201
- Exam Name: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
- Certification Provider: Cisco
- Latest update: Apr 09,2025
What are the two characteristics of the full packet captures? (Choose two.)
- A . Identifying network loops and collision domains.
- B . Troubleshooting the cause of security and performance issues.
- C . Reassembling fragmented traffic from raw data.
- D . Detecting common hardware faults and identify faulty assets.
- E . Providing a historical record of a network transaction.
Which two components reduce the attack surface on an endpoint? (Choose two.)
- A . secure boot
- B . load balancing
- C . increased audit log levels
- D . restricting USB ports
- E . full packet captures at the endpoint
When trying to evade IDS/IPS devices, which mechanism allows the user to make the data incomprehensible without a specific key, certificate, or password?
- A . fragmentation
- B . pivoting
- C . encryption
- D . stenography
C
Explanation:
https://techdifferences.com/difference-between-steganography-and-cryptography.html#:~:text=The%20steganography%20and%20cryptography%20are,the%20structure %20of%20the%20message.
One of the objectives of information security is to protect the CIA of information and systems.
What does CIA mean in this context?
- A . confidentiality, identity, and authorization
- B . confidentiality, integrity, and authorization
- C . confidentiality, identity, and availability
- D . confidentiality, integrity, and availability
Refer to the exhibit.
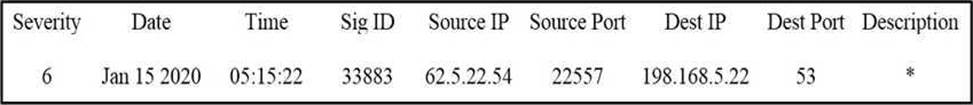
Which type of log is displayed?
- A . IDS
- B . proxy
- C . NetFlow
- D . sys
A
Explanation:
You also see the 5-tuple in IPS events, NetFlow records, and other event data. In fact, on the exam you may need to differentiate between a firewall log versus a traditional IPS or IDS event. One of the things to remember is that traditional IDS and IPS use signatures, so an easy way to differentiate is by looking for a signature ID (SigID). If you see a signature ID, then most definitely the event is a traditional IPS or IDS event.
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
- A . The RST flag confirms the beginning of the TCP connection, and the ACK flag responds when the data for the payload is complete
- B . The ACK flag confirms the beginning of the TCP connection, and the RST flag responds when the data for the payload is complete
- C . The RST flag confirms the receipt of the prior segment, and the ACK flag allows for the spontaneous termination of a connection
- D . The ACK flag confirms the receipt of the prior segment, and the RST flag allows for the spontaneous termination of a connection
What is the difference between an attack vector and attack surface?
- A . An attack surface identifies vulnerabilities that require user input or validation; and an attack vector identifies vulnerabilities that are independent of user actions.
- B . An attack vector identifies components that can be exploited, and an attack surface identifies the potential path an attack can take to penetrate the network.
- C . An attack surface recognizes which network parts are vulnerable to an attack; and an attack vector identifies which attacks are possible with these vulnerabilities.
- D . An attack vector identifies the potential outcomes of an attack; and an attack surface launches an attack using several methods against the identified vulnerabilities.
An investigator is examining a copy of an ISO file that is stored in CDFS format.
What type of evidence is this file?
- A . data from a CD copied using Mac-based system
- B . data from a CD copied using Linux system
- C . data from a DVD copied using Windows system
- D . data from a CD copied using Windows
B
Explanation:
CDfs is a virtual file system for Unix-like operating systems; it provides access to data and audio tracks on Compact Discs. When the CDfs driver mounts a Compact Disc, it represents each track as a file. This is consistent with the Unix convention "everything is a file". Source: https://en.wikipedia.org/wiki/CDfs
What is a difference between SOAR and SIEM?
- A . SOAR platforms are used for threat and vulnerability management, but SIEM applications are not
- B . SIEM applications are used for threat and vulnerability management, but SOAR platforms are not
- C . SOAR receives information from a single platform and delivers it to a SIEM
- D . SIEM receives information from a single platform and delivers it to a SOAR
Refer to the exhibit.
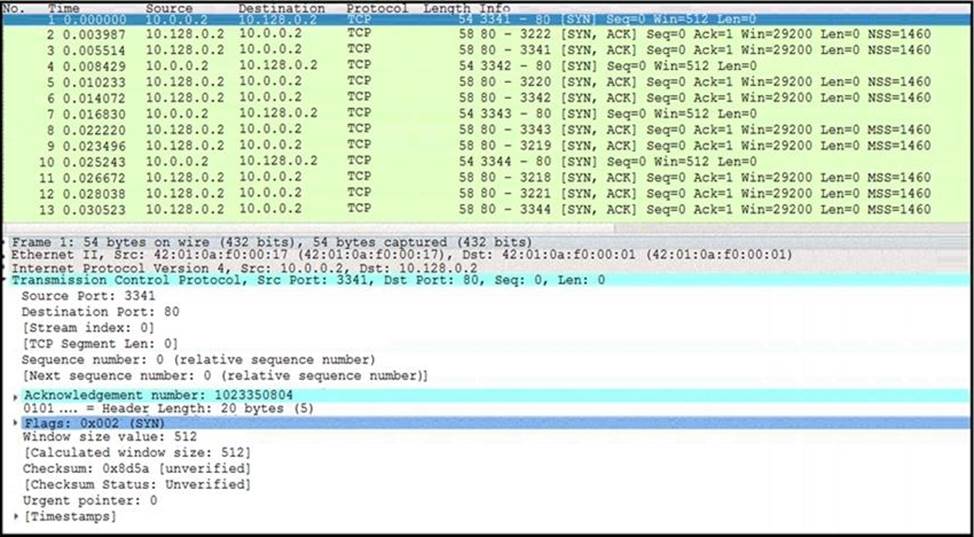
What is occurring in this network traffic?
- A . High rate of SYN packets being sent from a multiple source towards a single destination IP.
- B . High rate of ACK packets being sent from a single source IP towards multiple destination IPs.
- C . Flood of ACK packets coming from a single source IP to multiple destination IPs.
- D . Flood of SYN packets coming from a single source IP to a single destination IP.
