Amazon SCS-C02 Real Exam Questions
The questions for SCS-C02 were last updated at Apr 07,2025.
- Exam Code: SCS-C02
- Exam Name: AWS Certified Security - Specialty
- Certification Provider: Amazon
- Latest update: Apr 07,2025
A company wants to ensure that its IAM resources can be launched only in the us-east-1 and us-west-2 Regions.
What is the MOST operationally efficient solution that will prevent developers from launching Amazon EC2 instances in other Regions?
- A . Enable Amazon GuardDuty in all Regions. Create alerts to detect unauthorized activity outside us-east-1 and us-west-2.
- B . Use an organization in IAM Organizations. Attach an SCP that allows all actions when the IAM: Requested Region condition key is either us-east-1 or us-west-2. Delete the FullIAMAccess policy.
- C . Provision EC2 resources by using IAM Cloud Formation templates through IAM CodePipeline. Allow only the values of us-east-1 and us-west-2 in the IAM CloudFormation template’s parameters.
- D . Create an IAM Config rule to prevent unauthorized activity outside us-east-1 and us-west-2.
A company needs a forensic-logging solution for hundreds of applications running in Docker on Amazon EC2 The solution must perform real-time analytics on the togs must support the replay of messages and must persist the logs.
Which IAM services should be used to meet these requirements? (Select TWO)
- A . Amazon Athena
- B . Amazon Kinesis
- C . Amazon SQS
- D . Amazon Elasticsearch
- E . Amazon EMR
A company hosts an application on Amazon EC2 that is subject to specific rules for regulatory compliance. One rule states that traffic to and from the workload must be inspected for network-level attacks. This involves inspecting the whole packet.
To comply with this regulatory rule, a security engineer must install intrusion detection software on a c5n.4xlarge EC2 instance. The engineer must then configure the software to monitor traffic to and from the application instances.
What should the security engineer do next?
- A . Place the network interface in promiscuous mode to capture the traffic.
- B . Configure VPC Flow Logs to send traffic to the monitoring EC2 instance using a Network Load Balancer.
- C . Configure VPC traffic mirroring to send traffic to the monitoring EC2 instance using a Network Load Balancer.
- D . Use Amazon Inspector to detect network-level attacks and trigger an IAM Lambda function to send the suspicious packets to the EC2 instance.
A company that uses AWS Organizations wants to see AWS Security Hub findings for many AWS accounts and AWS Regions. Some of the accounts are in the company’s organization, and some accounts are in organizations that the company manages for customers. Although the company can see findings in the Security Hub administrator account for accounts in the company’s organization, there are no findings from accounts in other organizations.
Which combination of steps should the company take to see findings from accounts that are outside the organization that includes the Security Hub administrator account? (Select TWO.)
- A . Use a designated administration account to automatically set up member accounts.
- B . Create the AWS Service Role ForSecurrty Hub service-linked rote for Security Hub.
- C . Send an administration request from the member accounts.
- D . Enable Security Hub for all member accounts.
- E . Send invitations to accounts that are outside the company’s organization from the Security Hub administrator account.
A company stores sensitive documents in Amazon S3 by using server-side encryption with an IAM Key Management Service (IAM KMS) CMK. A new requirement mandates that the CMK that is used for these documents can be used only for S3 actions.
Which statement should the company add to the key policy to meet this requirement?
A)
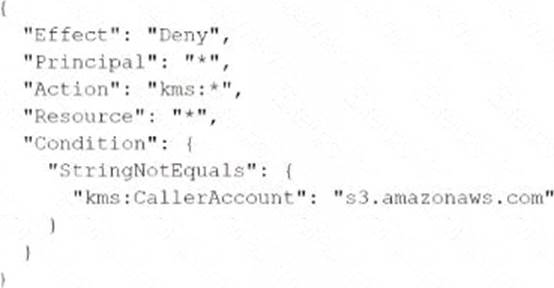
B)

C
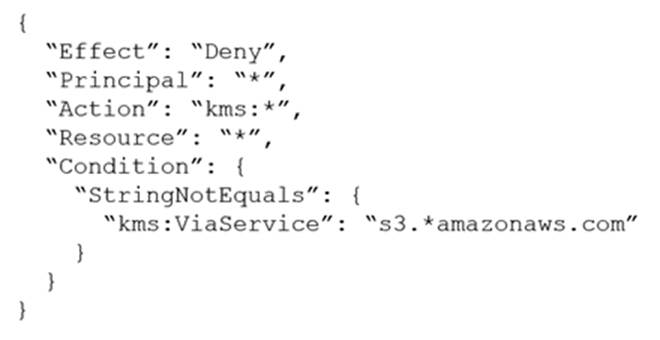
- A . Option A
- B . Option B
- C . Option C
An application team wants to use IAM Certificate Manager (ACM) to request public certificates to ensure that data is secured in transit. The domains that are being used are not currently hosted on Amazon Route 53
The application team wants to use an IAM managed distribution and caching solution to optimize requests to its systems and provide better points of presence to customers The distribution solution will use a primary domain name that is customized The distribution solution also will use several alternative domain names The certificates must renew automatically over an indefinite period of time
Which combination of steps should the application team take to deploy this architecture? (Select THREE.)
- A . Request a certificate (torn ACM in the us-west-2 Region Add the domain names that the certificate will secure
- B . Send an email message to the domain administrators to request vacation of the domains for ACM
- C . Request validation of the domains for ACM through DNS Insert CNAME records into each domain’s DNS zone
- D . Create an Application Load Balancer for me caching solution Select the newly requested certificate from ACM to be used for secure connections
- E . Create an Amazon CloudFront distribution for the caching solution Enter the main CNAME record as the Origin Name Enter the subdomain names or alternate names in the Alternate Domain Names Distribution Settings Select the newly requested certificate from ACM to be used for secure connections
- F . Request a certificate from ACM in the us-east-1 Region Add the domain names that the certificate wil secure
A security engineer is using AWS Organizations and wants to optimize SCPs. The security engineer needs to ensure that the SCPs conform to best practices.
Which approach should the security engineer take to meet this requirement?
- A . Use AWS IAM Access Analyzer to analyze the policies. View the findings from policy validation checks.
- B . Review AWS Trusted Advisor checks for all accounts in the organization.
- C . Set up AWS Audit Manager. Run an assessment for all AWS Regions for all accounts.
- D . Ensure that Amazon Inspector agents are installed on all Amazon EC2 in-stances in all accounts.
A developer 15 building a serverless application hosted on IAM that uses Amazon Redshift in a data store. The application has separate modules for read/write and read-only functionality. The modules need their own database users tor compliance reasons.
Which combination of steps should a security engineer implement to grant appropriate access’ (Select TWO)
- A . Configure cluster security groups for each application module to control access to database users that are required for read-only and read/write.
- B . Configure a VPC endpoint for Amazon Redshift Configure an endpoint policy that maps database users to each application module, and allow access to the tables that are required for read-only and read/write
- C . Configure an IAM poky for each module Specify the ARN of an Amazon Redshift database user that allows the GetClusterCredentials API call
- D . Create focal database users for each module
- E . Configure an IAM policy for each module Specify the ARN of an IAM user that allows the GetClusterCredentials API call
A company has an application that uses an Amazon RDS PostgreSQL database. The company is developing an application feature that will store sensitive information for an individual in the database.
During a security review of the environment, the company discovers that the RDS DB instance is not encrypting data at rest. The company needs a solution that will provide encryption at rest for all the existing data and for any new data that is entered for an individual.
Which combination of options can the company use to meet these requirements? (Select TWO.)
- A . Create a snapshot of the DB instance. Copy the snapshot to a new snapshot, and enable encryption for the copy process. Use the new snapshot to restore the DB instance.
- B . Modify the configuration of the DB instance by enabling encryption. Create a snapshot of the DB instance. Use the snapshot to restore the DB instance.
- C . Use IAM Key Management Service (IAM KMS) to create a new default IAM managed awards key. Select this key as the encryption key for operations with Amazon RDS.
- D . Use IAM Key Management Service (IAM KMS] to create a new CMK. Select this key as the encryption key for operations with Amazon RDS.
- E . Create a snapshot of the DB instance. Enable encryption on the snapshoVUse the snapshot to restore the DB instance.
A startup company is using a single AWS account that has resources in a single AWS Region. A security engineer configures an AWS Cloud Trail trail in the same Region to deliver log files to an Amazon S3 bucket by using the AWS CLI.
Because of expansion, the company adds resources in multiple Regions. The security engineer notices that the logs from the new Regions are not reaching the S3 bucket.
What should the security engineer do to fix this issue with the LEAST amount of operational overhead?
- A . Create a new CloudTrail trail. Select the new Regions where the company added resources.
- B . Change the S3 bucket to receive notifications to track all actions from all Regions.
- C . Create a new CloudTrail trail that applies to all Regions.
- D . Change the existing CloudTrail trail so that it applies to all Regions.
