Huawei H12-725_V4.0-ENU Real Exam Questions
The questions for H12-725_V4.0-ENU were last updated at Mar 31,2025.
- Exam Code: H12-725_V4.0-ENU
- Exam Name: HCIP-Security V4.0
- Certification Provider: Huawei
- Latest update: Mar 31,2025
When a visitor comes to the enterprise, while facilitating visitor access, it is necessary to control the visitor’s access behavior.
For this kind of visitor scenario, which of the following authentication methods is generally recommended?
- A . MAC bypass authentication
- B . Portal authentication
- C . 802.1X authentication
- D . MAC authentication
Which of the following is not part of the consistency check of dual-machine hot standby?
- A . Interface address
- B . NAT configuration
- C . Bandwidth Policy
- D . Security policy
Which of the following descriptions of the email content filtering operating mechanism is incorrect?
- A . The firewall first needs to identify the traffic to be filtered based on matching conditions.
- B . When a POP3 or IMAP message is detected, if it is determined to be an illegal email, the firewall’s response action can be to send an alarm message or block the email.
- C . Email content filtering is only detected in the outbound direction
- D . After the firewall filters out email traffic, it then checks the email address and attachment size to identify illegal emails.
WAF device’s working mode does not include which of the following?
- A . Forward proxy
- B . Reverse proxy
- C . Bridge mode
- D . Transparent proxy
Which item does the authentication protocol of Portal authentication not include?
- A . EAP protocol
- B . HTTP protocol
- C . Portal protocol
- D . HTTPS protocol
When IPSec uses certificate authentication, it is necessary to verify the legitimacy of the peer certificate. Which of the following is not a factor that needs to be considered to verify the legitimacy of the certificate?
- A . Whether the certificate is applied for in the same way
- B . Whether the certificate is within the validity period
- C . Whether the certificate is located in the CRL repository
- D . Whether the certificate is issued by the same CA
Which of the following statements about the features of the firewall hot standby system version upgrade is incorrect?
- A . When a bug occurs in the live network fire protection system version, the system version needs to be upgraded.
- B . When the existing network fire protection system version does not support certain features, the system version needs to be upgraded.
- C . Version upgrade has requirements for the device model and version before the upgrade
- D . When upgrading the dual-machine hot audio version, the rule of thumb is to upgrade the Active device first, and then upgrade the Standby device.
As shown in the figure, IPSec tunnels are established between the headquarters and branches. To achieve IPSec traffic load sharing, at least how many IPSec tunnels need to be established?
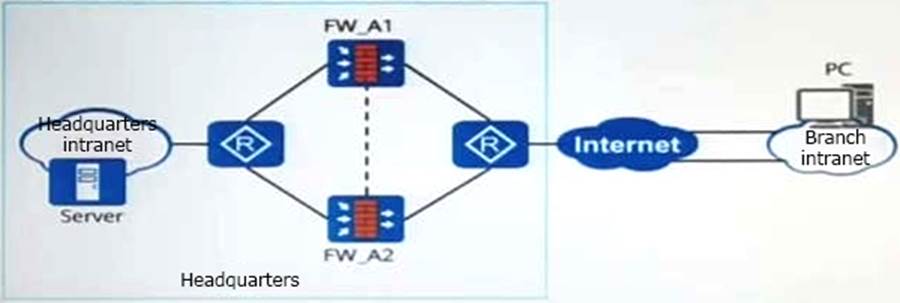
- A . 1
- B . 2
- C . 4
- D . 3
Bandwidth channels define specific bandwidth resources and are the basis for bandwidth management.
Which of the following is a resource that can be defined in a bandwidth channel?
- A . Bandwidth policy
- B . Daily traffic quota
- C . Egress bandwidth restrictions
- D . Strategic exclusivity
Which of the following is a method to prevent Tracert packet attacks?
- A . Discard IP packets with time offset
- B . Discard the detected ICMP messages or UDP messages that have expired, or the destination port is unreachable.
- C . Users can configure the maximum length of ICP packets allowed to pass according to actual network needs. When the length of the actual IP packet exceeds this value, the packet will be discarded.
- D . Discard ICMP unreachable messages and record attack logs
