DELL EMC D-ISM-FN-23 Real Exam Questions
The questions for D-ISM-FN-23 were last updated at Apr 02,2025.
- Exam Code: D-ISM-FN-23
- Exam Name: Dell Information Storage and Management Foundations 2023
- Certification Provider: DELL EMC
- Latest update: Apr 02,2025
What is a characteristic of an FC-AL implementation?
- A . Devices can be added and removed dynamically without any impact
- B . Supports connectivity up to 15 million nodes
- C . Requires at least one connectivity device
- D . Reserves one address for connecting an FC-SW port
A user lost access to a key VM due to a hardware failure. A proxy server regularly takes PIT snapshots of the VM to protect the data.
What type of data protection method is this called?
- A . Image-based
- B . Backup as a service
- C . Agent-based
- D . Local replication
An institution has made the decision to exit a client relationship due to anti-money laundering concerns. Prior to starting the close out process, the institution receives a written request from a law enforcement agency to keep the account open. The client is the subject of an ongoing investigation and law enforcement wants the institution to continue to monitor the account and report any suspicious activity.
What is primary consideration the institution should keep in mind when deciding whether to agree to this request?
- A . The anticipated cost of complying with the law enforcement request
- B . The number of suspicious transaction reports previously filed on the client
- C . The fact that the institution has a solid record in complying with law enforcement requests
- D . Whether the institution can continue to meet its regulatory obligations with the accounts open
Under the IaaS model, which elements are managed by the provider?
- A . Applications
Data
OS - B . Applications
Middleware
Runtime - C . Data
Servers
Networking - D . Virtualization
Servers
Networking
A company plans to deploy a new application in their environment. The new application requires 2 TB of storage space. During peak workloads, the application is expected to generate 4500 IOPS with a typical I/O size of 4 KB. The capacity of each available disk drive is 250 GB. In addition, the maximum number of IOPS a drive can perform at with a 70% utilization is 90 IOPS.
What is the minimum number of disk drives needed to meet the application’s capacity and performance requirements for a RAID 0 configuration?
- A . 8
- B . 40
- C . 50
- D . 70
Which type of storage device does the “X” represent in the exhibit?
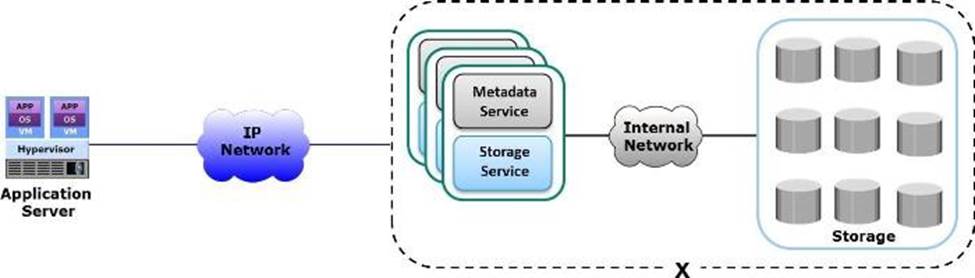
- A . Object-based
- B . Block-based
- C . File-based
- D . Unified-based
Which of the following are key fault tolerance techniques? (Choose two)
- A . RAID
- B . Data deduplication
- C . Load balancing
- D . Data archiving
What are the essential components of an object in an object-based storage system?
- A . File path, object ID, data, and filename
- B . Object ID, metadata, file path, and LUN ID
- C . Data, user-defined attributes, metadata, and object ID
- D . LUN ID, data, object ID, and user-defined attributes
What is an accurate statement about full volume replication?
- A . Target device is at least as large as the source device
- B . Target device requires only a fraction of the space used by the source device
- C . Target device is accessible only after the replication session starts
- D . Target and source devices should be on different storage arrays
What is an accurate statement about three-way NDMP backup in a NAS environment?
- A . Backup device can be shared among multiple NAS heads
- B . Each NAS head should have a dedicated backup device
- C . Backup data traverses at least three NAS heads before reaching the backup device
- D . Backup is performed only when three or more NAS heads are present
