Microsoft AZ-500 Real Exam Questions
The questions for AZ-500 were last updated at Dec 22,2025.
- Exam Code: AZ-500
- Exam Name: Microsoft Azure Security Technologies
- Certification Provider: Microsoft
- Latest update: Dec 22,2025
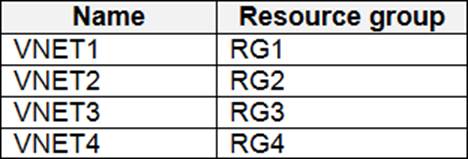
You have an Azure subscription named Sub1 that contains the resources shown in the following table.
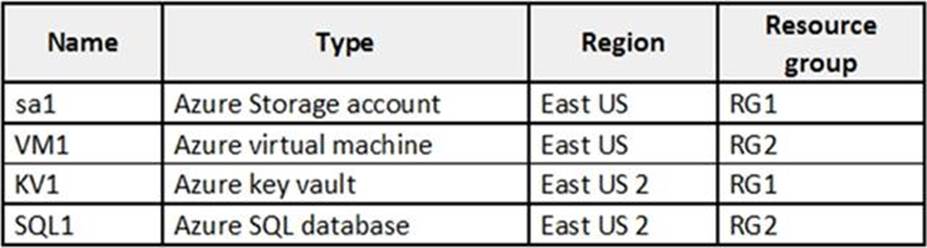
You need to ensure that you can provide VM1 with secure access to a database on SQL1 by using a contained database user.
What should you do?
- A . Enable a managed service identity on VM1.
- B . Create a secret in KV1.
- C . Configure a service endpoint on SQL1.
- D . Create a key in KV1.
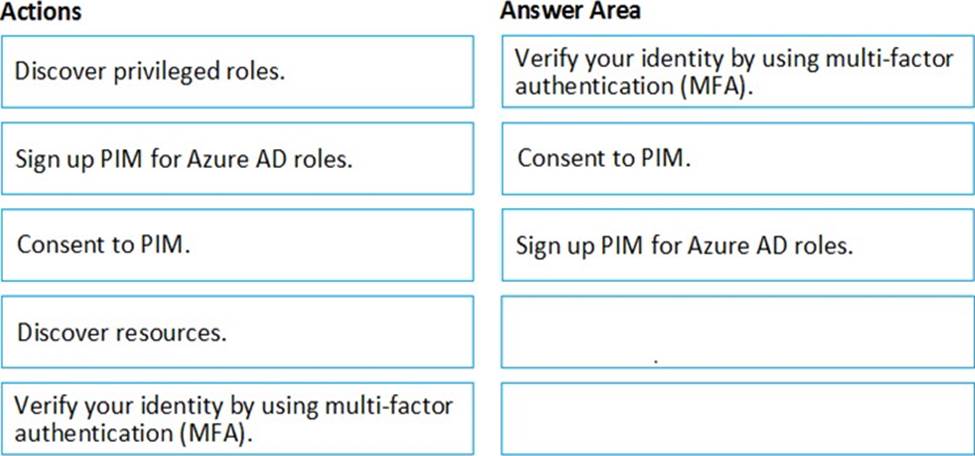
DRAG DROP
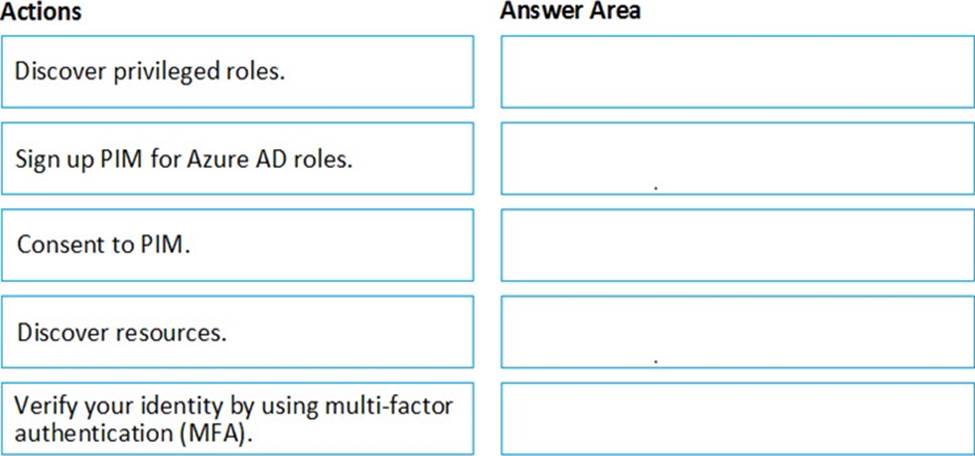
You create an Azure subscription with Azure AD Premium P2.
You need to ensure that you can use Azure Active Directory (Azure AD) Privileged Identity Management (PIM) to secure Azure roles.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
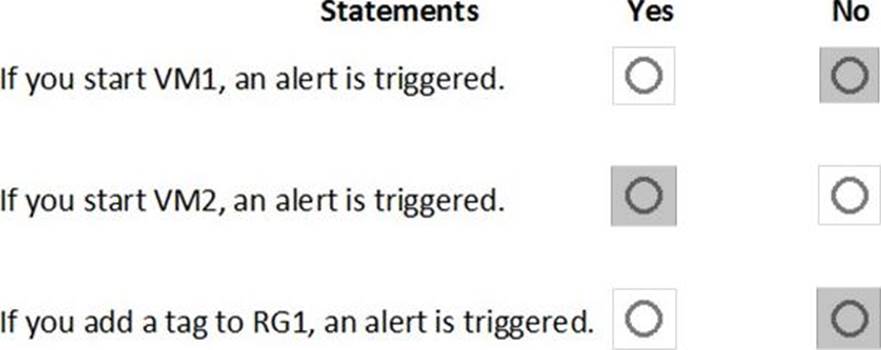
HOTSPOT
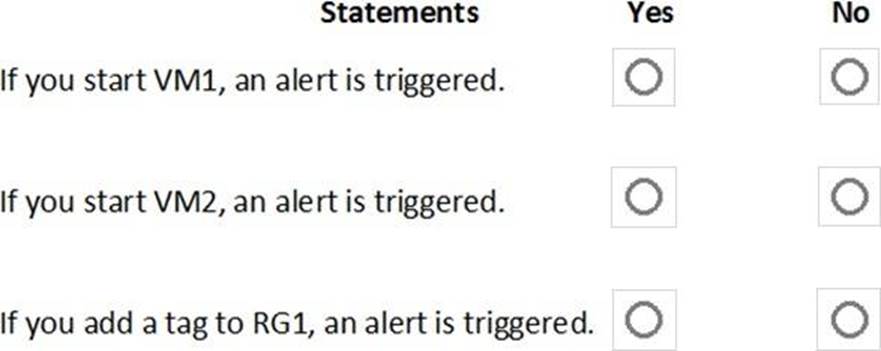
You create an alert rule that has the following settings:
✑ Resource: RG1
✑ Condition: All Administrative operations
✑ Actions: Action groups configured for this alert rule: ActionGroup1
✑ Alert rule name: Alert1
You create an action rule that has the following settings:
✑ Scope: VM1
✑ Filter criteria: Resource Type = "Virtual Machines"
✑ Define on this scope: Suppression
✑ Suppression config: From now (always)
✑ Name: ActionRule1
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Note: Each correct selection is worth one point.
You have an Azure SQL database.
You implement Always Encrypted.
You need to ensure that application developers can retrieve and decrypt data in the database.
Nantes’s of information should you provide to the developers? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
- A . a stored access policy
- B . a shared access signature (SAS)
- C . the column encryption key
- D . user credentials
- E . the column master key
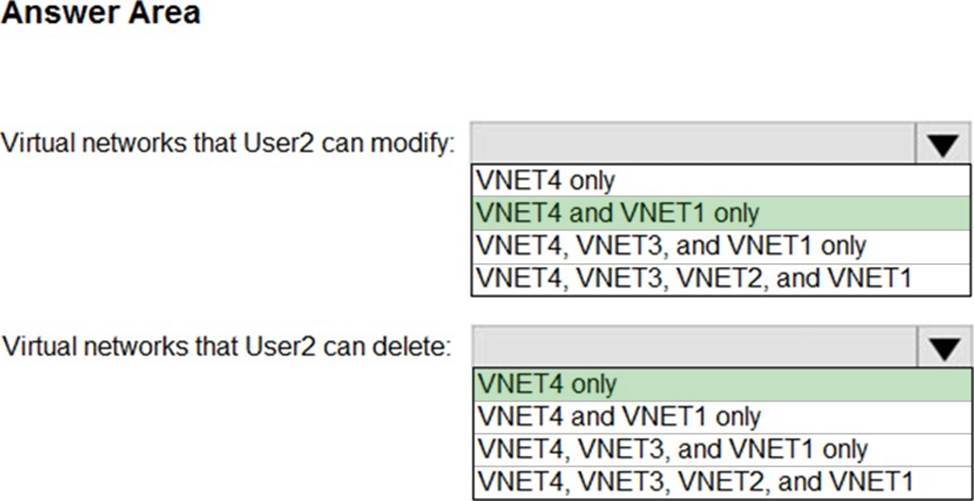
HOTSPOT
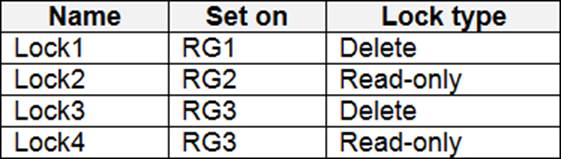
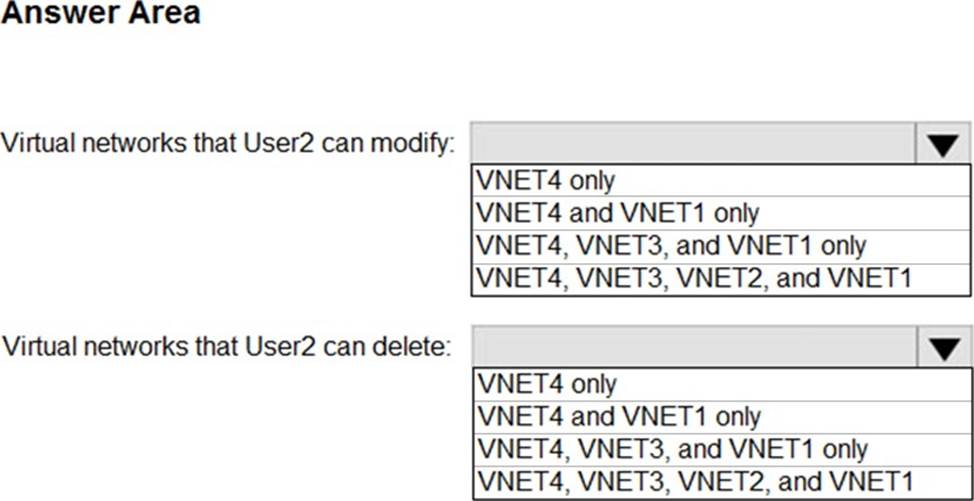
Which virtual networks in Sub1 can User2 modify and delete in their current state? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT
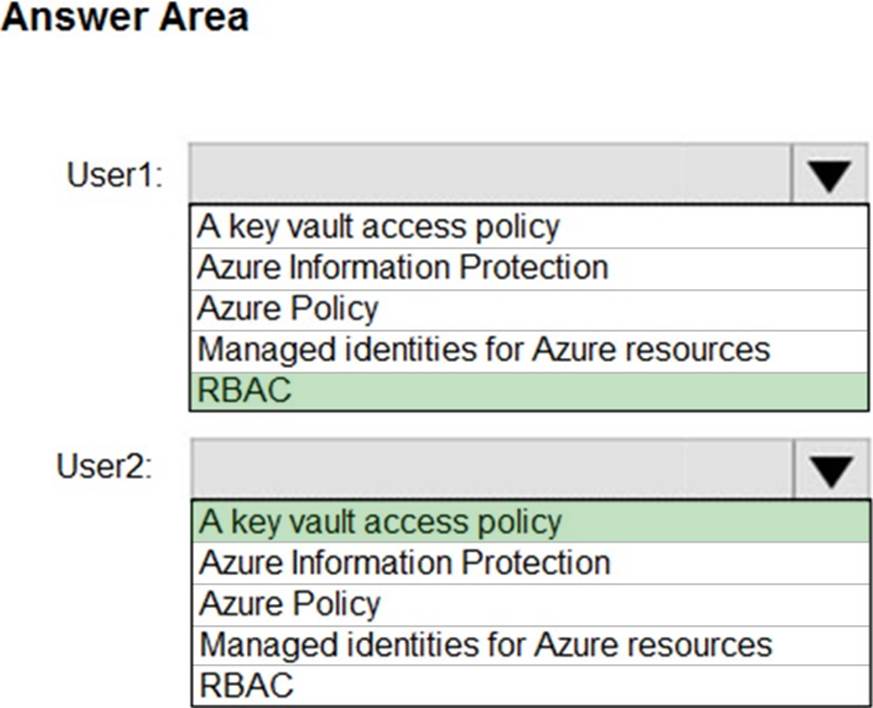
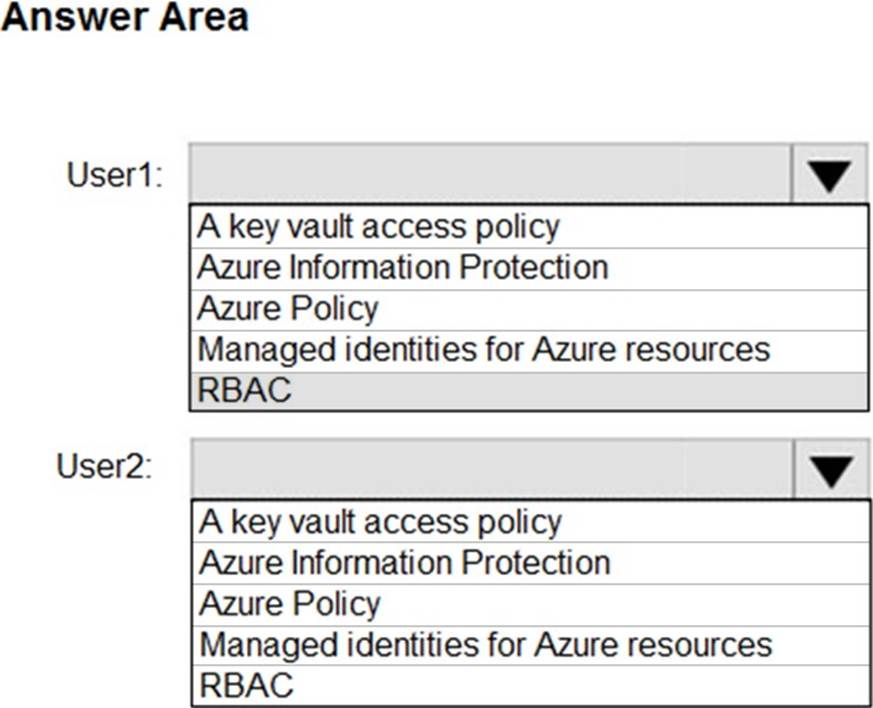
You have an Azure key vault.
You need to delegate administrative access to the key vault to meet the following requirements:
– Provide a user named User1 with the ability to set advanced access policies for the key vault.
– Provide a user named User2 with the ability to add and delete certificates in the key vault.
– Use the principle of least privilege.
What should you use to assign access to each user? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT
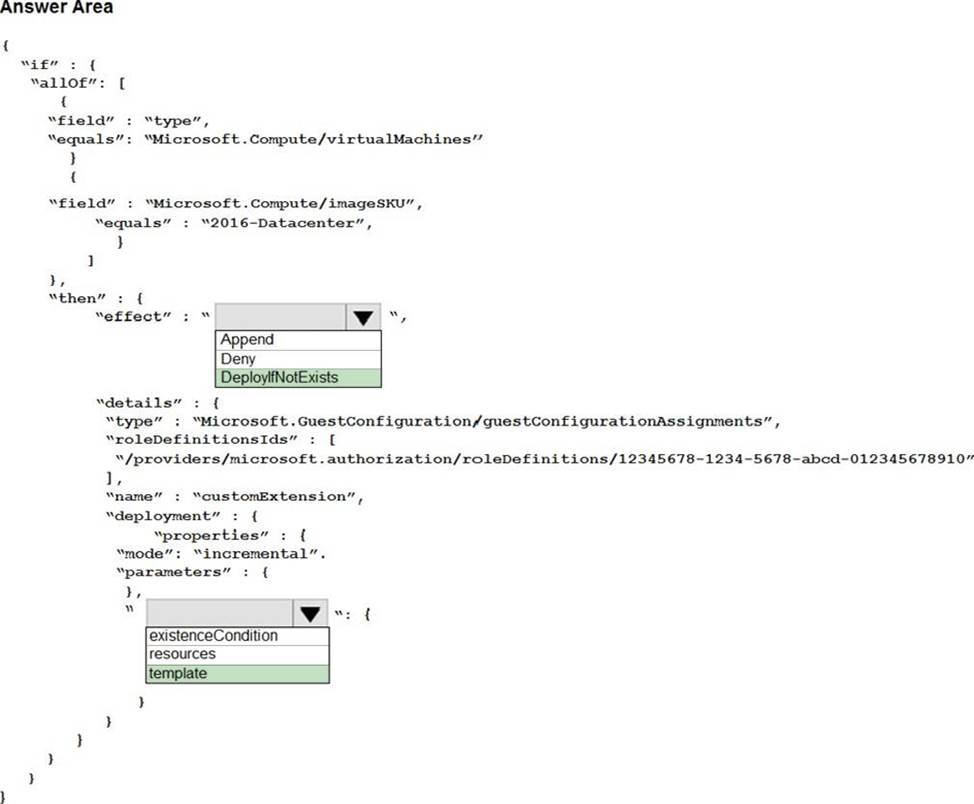
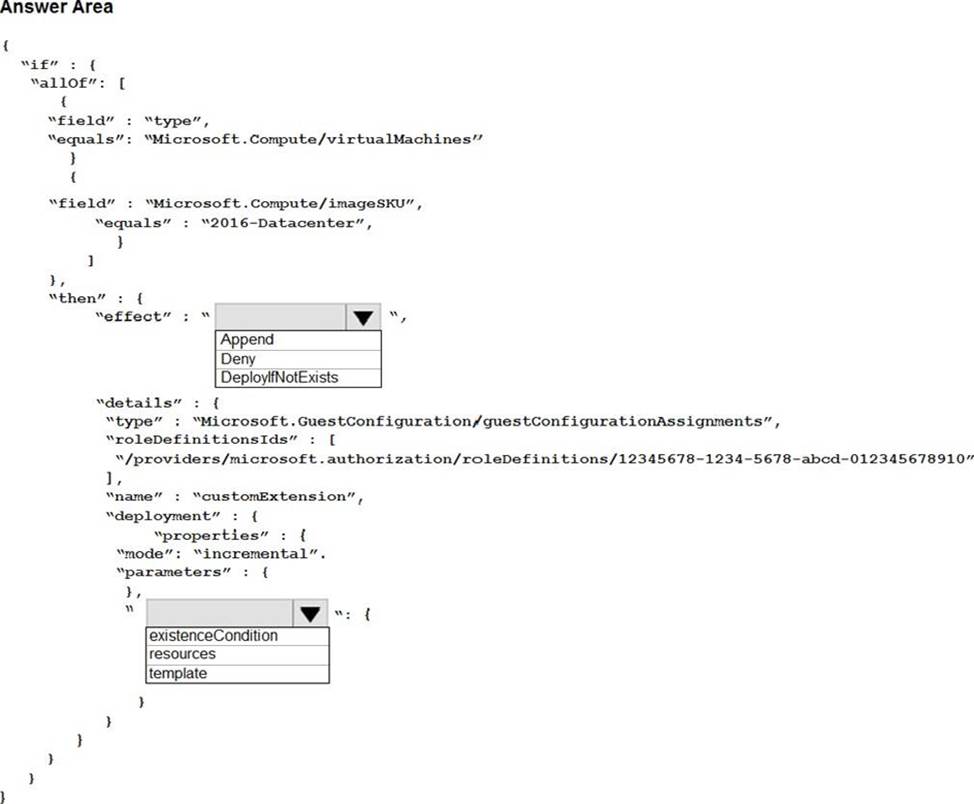
You have an Azure subscription. The subscription contains Azure virtual machines that run Windows Server 2016.
You need to implement a policy to ensure that each virtual machine has a custom antimalware virtual machine extension installed.
How should you complete the policy? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Subscription. The subscription contains 50 virtual machines that run Windows Server 2012 R2 or Windows Server 2016.
You need to deploy Microsoft Antimalware to the virtual machines.
Solution: You connect to each virtual machine and add a Windows feature.
Does this meet the goal?
- A . Yes
- B . No
You need to meet the technical requirements for VNetwork1.
What should you do first?
- A . Create a new subnet on VNetwork1.
- B . Remove the NSGs from Subnet11 and Subnet13.
- C . Associate an NSG to Subnet12.
- D . Configure DDoS protection for VNetwork1.
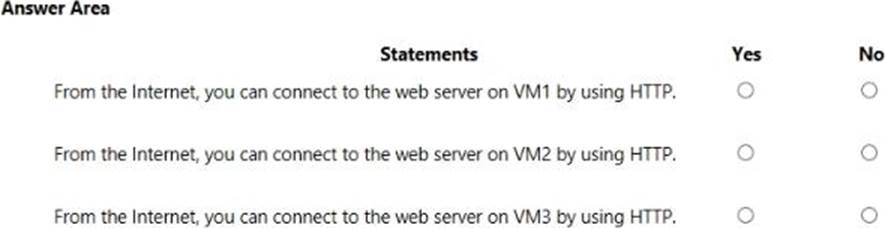
HOTSPOT
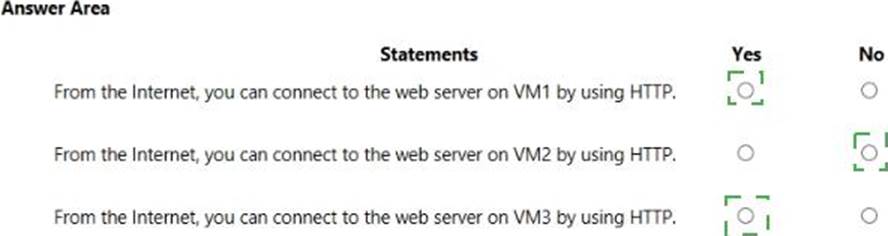
You are evaluating the security of VM1, VM2, and VM3 in Sub2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.