CompTIA SY0-601 Real Exam Questions
The questions for SY0-601 were last updated at Apr 13,2025.
- Exam Code: SY0-601
- Exam Name: CompTIA Security+ Exam
- Certification Provider: CompTIA
- Latest update: Apr 13,2025
An organization’s Chief Information Security Officer is creating a position that will be responsible for implementing technical controls to protect data, including ensuring backups are properly maintained.
Which of the following roles would MOST likely include these responsibilities?
- A . Data protection officer
- B . Data owner
- C . Backup administrator
- D . Data custodian
- E . Internal auditor
A company wants to modify its current backup strategy to modify its current backup strategy to minimize the number of backups that would need to be restored in case of data loss.
Which of the following would be the BEST backup strategy
- A . Incremental backups followed by differential backups
- B . Full backups followed by incremental backups
- C . Delta backups followed by differential backups
- D . Incremental backups followed by delta backups
- E . Full backup followed by different backups
Which of the following conditions impacts data sovereignty?
- A . Rights management
- B . Criminal investigations
- C . Healthcare data
- D . International operations
The Chief Technology Officer of a local college would like visitors to utilize the school’s WiFi but must be able to associate potential malicious activity to a specific person.
Which of the following would BEST allow this objective to be met?
- A . Requiring all new, on-site visitors to configure their devices to use WPS
- B . Implementing a new SSID for every event hosted by the college that has visitors
- C . Creating a unique PSK for every visitor when they arrive at the reception area
- D . Deploying a captive portal to capture visitors’ MAC addresses and names
A security engineer needs to build @ solution to satisfy regulatory requirements that stale certain critical servers must be accessed using MFA However, the critical servers are older and are unable to support the addition of MFA.
Which of the following will the engineer MOST likely use to achieve this objective?
- A . A forward proxy
- B . A stateful firewall
- C . A jump server
- D . A port tap
A large enterprise has moved all its data to the cloud behind strong authentication and encryption. A sales director recently had a
laptop stolen, and later, enterprise data was found to have been compromised from a local database.
Which of the following was the
MOST likely cause?
- A . Shadow IT
- B . Credential stuffing
- C . SQL injection
- D . Man in the browser
- E . Bluejacking
A security analyst must enforce policies to harden an MDM infrastructure.
The requirements are as follows:
* Ensure mobile devices can be tracked and wiped.
* Confirm mobile devices are encrypted.
Which of the following should the analyst enable on all the devices to meet these requirements?
- A . A Geofencing
- B . Biometric authentication
- C . Geolocation
- D . Geotagging
A security engineer is installing a WAF to protect the company’s website from malicious web requests over SSL.
Which of the following is needed to meet the objective?
- A . A reverse proxy
- B . A decryption certificate
- C . A spill-tunnel VPN
- D . Load-balanced servers
During a Chief Information Security Officer (CISO) convention to discuss security awareness, the attendees are provided with a network connection to use as a resource. As the convention progresses, one of the attendees starts to notice delays in the connection, and the HIIPS site requests are reverting to HTTP.
Which of the following BEST describes what is happening?
- A . Birthday collision on the certificate key
- B . DNS hijacking to reroute traffic
- C . Brute force to the access point
- D . ASSLILS downgrade
A security analyst has received several reports of an issue on an internal web application. Users state they are having to provide their credentials twice to log in. The analyst checks with the application team and notes this is not an expected behavior.
After looking at several logs, the analyst decides to run some commands on the gateway and obtains the following output:
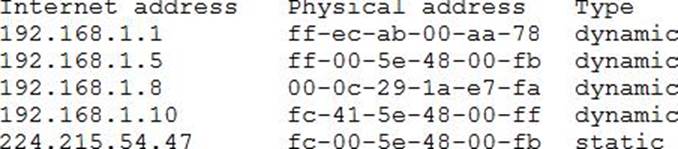
Which of the following BEST describes the attack the company is experiencing?
- A . MAC flooding
- B . URL redirection
- C . ARP poisoning
- D . DNS hijacking
